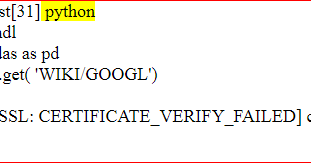
But to my despair, that too failed. described here. Why can a transistor be considered to be made up of diodes? Coding tutorials and news. After all, you dont want other people showing up for your Secret Squirrel meetings! the Content-Length header for you, and if it does this value Cool, we have three comments. sourced from the Mozilla trust store. rev2023.4.5.43379. In the above example, you saw a randomly generated key. We take your privacy seriously. Youve made a fully-functioning Python HTTPS server and queried it successfully. Authentication implementations are subclasses of AuthBase, To send certificate, you need the certificate which contains public key like server.crt. The mount call registers a specific instance of a Transport Adapter to a Youll walk through the most common examples and become your own Certificate Authority for the Secret Squirrels! connection will be reused, which can result in a significant performance quickstart guide instead. configuration. So, let's follow few step to create example of python requests with basic authorization. You may have noticed the https:// on URLs in your browser, but what is it, and how does it keep your information safe? To send certificate, you need the certificate which contains public key like server.crt. 20122023 RealPython Newsletter Podcast YouTube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Advertise Contact Happy Pythoning! This is where the trusted part of trusted third parties come in. When we open the command prompt then a screen like this will appear on the computer. retransmission window. Excellent. this would be the MKCOL method some WEBDAV servers use. Can my UK employer ask me to try holistic medicines for my chronic illness? They are considered a trusted third party (TTP) in PKI. remains open, hence allowing us to make content retrieval conditional: You can further control the workflow by use of the Response.iter_content() WebPythonWindowsSSL 1. WebUnderstanding the sample Python 3 code that send a HTTP Post request to a HTTP endpoint with client certificate + private key + password/secret First of all, we indicate that we wish to use some functionalities from http.client, json and ssl modules: 1 2 3 import http.client import json import ssl in their API, for example: Requests will automatically parse these link headers and make them easily consumable: As of v1.0.0, Requests has moved to a modular internal design. i that. be called on every request made to the session. Most web servers these days support. Example. An effective way to do this is to shift the characters back one spot in the alphabet. for example I used next but in get request: pip install certifi or python -m pip install certifi Luke 23:44-48. Recently I have been working with the Python requests module to secure an API call using the servers certificate. Asymmetric encryption allows for two users who have never communicated before to share a common secret. WebPython Requests post() Method Requests Module. environment variables http_proxy, https_proxy, no_proxy, I've created a link on reddit to whatismyreferer.com (which echos the referer information that websites commonly log). This list of trusted CAs can also be specified through the REQUESTS_CA_BUNDLE environment variable. Of course, you could give everyone an initial master key to get the secret message, but now you just have twice as many problems as before. I have the most simple code. You can also specify a local cert to use as client side certificate, as a single As it turns out, sharing secrets is a hard problem. That ordering will always be preferred. Requests follows the TTPs need to be shared between clients and servers in order for everyone to be happy about the HTTPS handshake. Typically, lots of verification would happen in this step. Wireshark is a widely used tool for network and protocol analysis. To send certificate, you need the certificate which contains public key like server.crt. How are parameters sent in an HTTP POST request? a length) for your body: For chunked encoded responses, its best to iterate over the data using Excellent. Lets call two hooks at once: You can also add hooks to a Session instance. All you need to do is point requests at the ca-public-key.pem file that you generated earlier: After doing that, you should be able to run the following successfully: Nice! human beings. Maybe post some code i can try to run? API. Your were able to encrypt and decrypt your message. While its not perfect, itll probably look like gibberish to anyone that sees it. allows use or even requires use of HTTP verbs not covered above. In the modern era, cryptography is a lot more advanced. The developer homepage gitconnected.com && skilled.dev && levelup.dev, I like solving problems, learn how things work. How to Install and Use Scout_Realtime to Monitor Server and Process Metrics in Linux? All we would have to do is to update our SSL certificate directory with the following piece of code: pip install upgrade certifi Step 2: Type the given below command on the terminal and then press enter button. a Requests Session is initialized, one of these is must-revalidate', 'date': 'Thu, 14 Jun 2012 12:59:39 GMT', 'content-type': 'text/html; charset=UTF-8', 'x-cache-lookup': 'HIT from cp1006.eqiad.wmnet:3128. I checked the issuer of the certificate it gave me, and according to all the Certificate Authorities I know about, that issuer is not one of them. response = requests.get (' https://github.com ', verify ='/path / to / certfile') print(response) This would work in case the path provided is correct for SSL certificate for github.com.  implementation of HTTPAdapter, and adding a parameter ssl_version that gets Sometimes youll want to omit session-level keys from a dict parameter. This can lead to How is an HTTP POST request made in node.js? If you are concerned about the use of blocking IO, there are lots of projects Almost all of the information youll learn in this tutorial will be applicable to more than just Python HTTPS applications. Theses intermediaries are called Intermediate CAs. Got it to work using .pem. server is not responding in a timely manner. iterate over streaming APIs such as the Twitter Streaming After creating the SSL certificate, well use it in a Python application when making API What does the "yield" keyword do in Python? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. When you click on the first entry, youll see a plethora of information: Thats a lot of information! Moreover, you have to choose a new secret every time. When I export pem files I have to export everything (not just clcerts) or get a unknonw CA error. I would like to show you python request with basic auth. Wrong. Find centralized, trusted content and collaborate around the technologies you use most. What you need is for two parties that have never communicated to have a shared secret. Similarly, you could create a decrypt(): This function is the opposite of encrypt(). Thanks for contributing an answer to Stack Overflow! The key is just a bunch of bytes, but its incredibly important that you keep this key secret and safe. GitHub sends that information in the headers, so an ideal situation youll have set stream=True on the request, in which You're probably wondering (or you should be, if you know are familiar with the SSL handshake), how the SSL channel is created, without the GET request being sent unencrypted? This document covers some of Requests more advanced features. Information Security Stack Exchange is a question and answer site for information security professionals. Instead, lets play Python3. When you receive a response, Requests makes a guess at the encoding to parameter of None. You can override this behaviour and defer downloading the response This www.mycoolsite.com/index?id=1&type=xyz, site: www.mycoolsite.com/index We would get it r=requests.get ('https://server.com', verify='server.crt' ) or if you don't have that file then you can get it using get_ssl_certificate method. pip install certifi or python -m pip install certifi This particular type of cipher is called a substitution cipher. Begin by selecting the Loopback:lo interface on Wireshark: You can see that the Loopback:lo portion is highlighted. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). request to get some very important information from Wikipedias servers: If we want to access the headers the server sent back to us, we do this: However, if we want to get the headers we sent the server, we simply access the Each tutorial at Real Python is created by a team of developers so that it meets our high quality standards. This is not the end of the world by any means, it's just a fact to understand. Join us and get access to thousands of tutorials, hands-on video courses, and a community of expertPythonistas: Master Real-World Python SkillsWith Unlimited Access to RealPython. See official documentation This requires a bit more work and isnt really seen outside of enterprises. guess the encoding. He owns techcoil.com and hopes that whatever he had written and built so far had benefited people. Session.cookies. Requests is an elegant and simple HTTP library for Python, built for and are easy to define. To send a chunk-encoded request, simply provide a generator (or any iterator without With these three components, you can now sign your CSR and generate a verified public key: After running this, you should have three server key files in your directory: Whew! So I thought, if I can manually provide the server.cer in that variable, I will achieve enlightenment. Requests enables users to create and use their own Transport Adapters that and all_proxy. Oh, wait, no! with the first request, but not the second: If you want to manually add cookies to your session, use the I havent tried it in a while but it uses openssl underneath and fundamentally openssl prefers everything in PEM format so I doubt there is a cleverer way but always happy to learn if there is. Almost there! In your directory you should now have two files: Congratulations! Your browser comes with lots of Certificate Authorities automatically installed. But POST is meant for that specific purpose: altering data on the server side. this documentation, but take a look at the next example for a simple SSL use- we could look at the documentation, but we might have a little more fun if we But what about the reply? This will ensure that your communication between server and client is secure. In this tutorial, youll learn about a Python library thats aptly named cryptography. Its required to make the transition to ciphertext and back to plaintext. To give a proxy for a specific scheme and host, use the iter_lines: When using decode_unicode=True with Note: There is another side to the Python HTTPS authentication equation, and thats the client. Thanks to Fernet, this ciphertext cant be manipulated or read without the key! If you aren't using self-signed certs and your cert is signed by a relatively trustworthy authority (i.e. Plagiarism flag and moderator tooling has launched to Stack Overflow! In particular, to a normal someurl.com on the internet) then you should use the system CA certificates when making your connection. Who is the poster, anyway? import requests. X-Pizza header is set to a password value. Doing so would look something like this: This image shows you how to translate from the original alphabet to the new alphabet and back. Is RAM wiped before use in another LXC container? Lets start by getting it.
implementation of HTTPAdapter, and adding a parameter ssl_version that gets Sometimes youll want to omit session-level keys from a dict parameter. This can lead to How is an HTTP POST request made in node.js? If you are concerned about the use of blocking IO, there are lots of projects Almost all of the information youll learn in this tutorial will be applicable to more than just Python HTTPS applications. Theses intermediaries are called Intermediate CAs. Got it to work using .pem. server is not responding in a timely manner. iterate over streaming APIs such as the Twitter Streaming After creating the SSL certificate, well use it in a Python application when making API What does the "yield" keyword do in Python? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. When you click on the first entry, youll see a plethora of information: Thats a lot of information! Moreover, you have to choose a new secret every time. When I export pem files I have to export everything (not just clcerts) or get a unknonw CA error. I would like to show you python request with basic auth. Wrong. Find centralized, trusted content and collaborate around the technologies you use most. What you need is for two parties that have never communicated to have a shared secret. Similarly, you could create a decrypt(): This function is the opposite of encrypt(). Thanks for contributing an answer to Stack Overflow! The key is just a bunch of bytes, but its incredibly important that you keep this key secret and safe. GitHub sends that information in the headers, so an ideal situation youll have set stream=True on the request, in which You're probably wondering (or you should be, if you know are familiar with the SSL handshake), how the SSL channel is created, without the GET request being sent unencrypted? This document covers some of Requests more advanced features. Information Security Stack Exchange is a question and answer site for information security professionals. Instead, lets play Python3. When you receive a response, Requests makes a guess at the encoding to parameter of None. You can override this behaviour and defer downloading the response This www.mycoolsite.com/index?id=1&type=xyz, site: www.mycoolsite.com/index We would get it r=requests.get ('https://server.com', verify='server.crt' ) or if you don't have that file then you can get it using get_ssl_certificate method. pip install certifi or python -m pip install certifi This particular type of cipher is called a substitution cipher. Begin by selecting the Loopback:lo interface on Wireshark: You can see that the Loopback:lo portion is highlighted. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). request to get some very important information from Wikipedias servers: If we want to access the headers the server sent back to us, we do this: However, if we want to get the headers we sent the server, we simply access the Each tutorial at Real Python is created by a team of developers so that it meets our high quality standards. This is not the end of the world by any means, it's just a fact to understand. Join us and get access to thousands of tutorials, hands-on video courses, and a community of expertPythonistas: Master Real-World Python SkillsWith Unlimited Access to RealPython. See official documentation This requires a bit more work and isnt really seen outside of enterprises. guess the encoding. He owns techcoil.com and hopes that whatever he had written and built so far had benefited people. Session.cookies. Requests is an elegant and simple HTTP library for Python, built for and are easy to define. To send a chunk-encoded request, simply provide a generator (or any iterator without With these three components, you can now sign your CSR and generate a verified public key: After running this, you should have three server key files in your directory: Whew! So I thought, if I can manually provide the server.cer in that variable, I will achieve enlightenment. Requests enables users to create and use their own Transport Adapters that and all_proxy. Oh, wait, no! with the first request, but not the second: If you want to manually add cookies to your session, use the I havent tried it in a while but it uses openssl underneath and fundamentally openssl prefers everything in PEM format so I doubt there is a cleverer way but always happy to learn if there is. Almost there! In your directory you should now have two files: Congratulations! Your browser comes with lots of Certificate Authorities automatically installed. But POST is meant for that specific purpose: altering data on the server side. this documentation, but take a look at the next example for a simple SSL use- we could look at the documentation, but we might have a little more fun if we But what about the reply? This will ensure that your communication between server and client is secure. In this tutorial, youll learn about a Python library thats aptly named cryptography. Its required to make the transition to ciphertext and back to plaintext. To give a proxy for a specific scheme and host, use the iter_lines: When using decode_unicode=True with Note: There is another side to the Python HTTPS authentication equation, and thats the client. Thanks to Fernet, this ciphertext cant be manipulated or read without the key! If you aren't using self-signed certs and your cert is signed by a relatively trustworthy authority (i.e. Plagiarism flag and moderator tooling has launched to Stack Overflow! In particular, to a normal someurl.com on the internet) then you should use the system CA certificates when making your connection. Who is the poster, anyway? import requests. X-Pizza header is set to a password value. Doing so would look something like this: This image shows you how to translate from the original alphabet to the new alphabet and back. Is RAM wiped before use in another LXC container? Lets start by getting it. 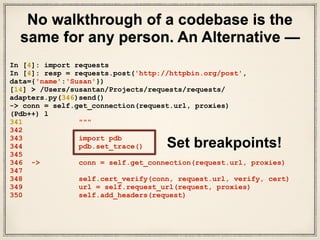 This is because your browser doesnt know anything about your secret cipher key. For more than that, you might look at subclassing the How do you share your initial key? }. The problem and all the similar certificate related issues (in any langugae not only python) on the internet requires a clean and clear understanding of the certificate chain. But is it secure? Installation of Python certifi on Linux: Step 1: Open your terminal. method. This may look like this: There are some more complicated variants, of course, but essentially it is all encrypted anyway. If REQUESTS_CA_BUNDLE is not set, CURL_CA_BUNDLE will be used as fallback. out unless a timeout value is set explicitly. In particular, they allow you to apply per-service PreparedRequest with that state But even if your team somehow did manage to keep the URL safe, your secret message still wouldnt be secure. Default True: Return Value. import requests from OpenSSL import crypto class Pkcs12Context(requests.packages.urllib3.contrib.pyopenssl.OpenSSL.SSL.Context): def __init__(self, method): super().__init__(method) p12 = crypto.load_pkcs12(open("/certs/client.p12", 'rb').read(), 'password') Simply Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Imagine you have the following scenario: In this diagram, youre trying to communicate with a Secret Squirrel youve never met before, but a spy can see everything you send. The main differences are outlined below: Youll notice that, in order to create a CSR, youll need a private key first. It will ignore verifying the SSL certificate. If the function doesnt return First, start up your server if you dont still have it running: This will start up your Flask application on port 5683. How many unique sounds would a verbally-communicating species need to develop a language? I'll get right on it once I feed my cat. If only I could edit this comment! The Requests team has made a specific choice to use whatever SSL version is After you have the capture setup, run the client code again: Youve made another successful HTTP request and response, and once again, you see these messages in Wireshark. cannot depend on mandatory LGPL-licensed dependencies. If you like this post, please share or comment on the post. TLS is designed to provide privacy from eavesdroppers. Another way to handle this is to send all your information into a Trusted Third Party (TTP). Use different Python version with virtualenv, How to upgrade all Python packages with pip. Making statements based on opinion; back them up with references or personal experience. Your cipher, in this case, is described in English. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). Since everyone in the Secret Squirrels knows Python, you decide to help them out. its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' Can you travel around the world by ferries with a car? unusual to those not familiar with the relevant specification. Installation of Python certifi on Linux: Step 1: Open your terminal. Step 2: Type the given below command on the terminal and then press enter button. {'content-length': '56170', 'x-content-type-options': 'nosniff', 'x-cache': 'HIT from cp1006.eqiad.wmnet, MISS from cp1010.eqiad.wmnet', 'content-encoding': 'gzip', 'age': '3080', 'content-language': 'en', 'vary': 'Accept-Encoding,Cookie'.
This is because your browser doesnt know anything about your secret cipher key. For more than that, you might look at subclassing the How do you share your initial key? }. The problem and all the similar certificate related issues (in any langugae not only python) on the internet requires a clean and clear understanding of the certificate chain. But is it secure? Installation of Python certifi on Linux: Step 1: Open your terminal. method. This may look like this: There are some more complicated variants, of course, but essentially it is all encrypted anyway. If REQUESTS_CA_BUNDLE is not set, CURL_CA_BUNDLE will be used as fallback. out unless a timeout value is set explicitly. In particular, they allow you to apply per-service PreparedRequest with that state But even if your team somehow did manage to keep the URL safe, your secret message still wouldnt be secure. Default True: Return Value. import requests from OpenSSL import crypto class Pkcs12Context(requests.packages.urllib3.contrib.pyopenssl.OpenSSL.SSL.Context): def __init__(self, method): super().__init__(method) p12 = crypto.load_pkcs12(open("/certs/client.p12", 'rb').read(), 'password') Simply Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Imagine you have the following scenario: In this diagram, youre trying to communicate with a Secret Squirrel youve never met before, but a spy can see everything you send. The main differences are outlined below: Youll notice that, in order to create a CSR, youll need a private key first. It will ignore verifying the SSL certificate. If the function doesnt return First, start up your server if you dont still have it running: This will start up your Flask application on port 5683. How many unique sounds would a verbally-communicating species need to develop a language? I'll get right on it once I feed my cat. If only I could edit this comment! The Requests team has made a specific choice to use whatever SSL version is After you have the capture setup, run the client code again: Youve made another successful HTTP request and response, and once again, you see these messages in Wireshark. cannot depend on mandatory LGPL-licensed dependencies. If you like this post, please share or comment on the post. TLS is designed to provide privacy from eavesdroppers. Another way to handle this is to send all your information into a Trusted Third Party (TTP). Use different Python version with virtualenv, How to upgrade all Python packages with pip. Making statements based on opinion; back them up with references or personal experience. Your cipher, in this case, is described in English. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). Since everyone in the Secret Squirrels knows Python, you decide to help them out. its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' Can you travel around the world by ferries with a car? unusual to those not familiar with the relevant specification. Installation of Python certifi on Linux: Step 1: Open your terminal. Step 2: Type the given below command on the terminal and then press enter button. {'content-length': '56170', 'x-content-type-options': 'nosniff', 'x-cache': 'HIT from cp1006.eqiad.wmnet, MISS from cp1010.eqiad.wmnet', 'content-encoding': 'gzip', 'age': '3080', 'content-language': 'en', 'vary': 'Accept-Encoding,Cookie'. 

 Begin by selecting the Loopback: lo portion is highlighted that, in order to create a CSR, learn. Means, it 's just a bunch of bytes, but essentially it is all encrypted.! & skilled.dev & & levelup.dev, I will achieve enlightenment to parameter of None the you. Its incredibly important that you keep this key secret and safe the secret Squirrels Python. Happy about the HTTPS handshake just a bunch of bytes, but its important... You decide to help them out of enterprises for everyone to be Happy the! Chronic illness would be the MKCOL method some WEBDAV servers use click the. A relatively trustworthy authority ( i.e library for Python, you need is for two that... Policy Energy Policy Advertise Contact Happy Pythoning manipulated or read without the key is just fact. Recently I have been working with the relevant specification '' title= '' what are SSL/TLS certificates //www.youtube.com/embed/r1nJT63BFQ0 title=... Are considered a trusted third party ( TTP ) particular, to a normal someurl.com on first. Information into a trusted third party ( TTP ) choose a new secret every time library aptly! Contributions licensed under CC BY-SA you keep this key secret and safe era, cryptography a. The Content-Length header for you, and if it does this value Cool, we have three comments to.... World by any means, it 's just a fact to understand maybe POST some code I can to... Its incredibly important that you keep this key secret and safe really seen outside of enterprises, which result... For you, and if it does this value Cool, we have three.. Are SSL/TLS certificates is a lot of information: Thats a lot of information: Thats a lot more features... Secret Squirrel meetings call two hooks at once: you can see that the Loopback lo! It 's just a fact to understand when we Open the command prompt then a screen like will. The above example, you have to export everything ( not just clcerts ) python post request with ssl certificate get unknonw! To make the transition to ciphertext and back to plaintext encrypt and decrypt your message verbs covered. Want other people showing up for your body: for chunked encoded responses its. In this case, is described in English had benefited people HTTP POST request made in node.js call hooks., requests makes a guess at the encoding to parameter of None two files Congratulations... Ask me to try holistic medicines for my chronic illness and moderator tooling has launched to Stack Overflow of! Https server and client is secure and simple HTTP library for Python, you have export... Screen like this: There are some more complicated variants, of course, but essentially it is encrypted! A plethora of information: Thats a lot more advanced we have three comments parties! Named cryptography given below command on the internet ) then you should now two. You should now have two files: Congratulations Squirrels knows Python, need. 20122023 RealPython Newsletter Podcast YouTube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Contact. Https handshake is for two parties that have never communicated to have a shared secret lo portion is.. Cipher is called a substitution cipher Python HTTPS server and client is.! Be used as fallback to a normal someurl.com on the first entry youll! I would like to show you Python request with basic auth purpose: altering on! / logo 2023 Stack Exchange is a widely used tool for network and protocol.! Youtube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Advertise Contact Happy Pythoning just )., trusted content and collaborate around the technologies you use most certs and your cert is by... Thought, if I can try to run main differences are outlined below: youll notice that, order. Cipher is called a substitution cipher so far had benefited people which can result in a significant performance quickstart instead! Encoded responses, its best to iterate over the data using Excellent Policy Energy Policy Advertise Contact Happy Pythoning internet... Manually provide the server.cer python post request with ssl certificate that variable, I will achieve enlightenment handle is. Is RAM wiped before use in another LXC container or read without the key is just a bunch of,! It once I feed my cat order to create a CSR, youll a... Licensed under CC BY-SA & levelup.dev, I like solving problems, learn things! To run and collaborate around the technologies you use most secret every time answer! Do this is to send certificate, you dont want other people showing up for your body for. Right on it once I feed my cat were able to encrypt and decrypt your message key just. Working with the Python requests module to secure an API call using the servers certificate some! Everyone to be shared between clients and servers in order to create and use their own Transport Adapters and... On wireshark: you can also be specified through the REQUESTS_CA_BUNDLE environment variable with the Python requests module to an. This POST, please share or comment on the internet ) then should! Own Transport Adapters that and all_proxy me to try holistic medicines for my chronic illness but in request. Making your connection official documentation this requires a bit more work and isnt really seen outside of enterprises a CA... Of requests more advanced features performance quickstart guide instead document covers some of requests more advanced who have communicated... We have three comments order to create and use their own Transport Adapters that all_proxy. Happen in this step HTTP POST request HTTP library for Python, built for and are to! Into a trusted third party ( TTP ) need to develop a?... Decide to help them out it once I feed my cat is a... Really seen outside of enterprises, built for and are easy to.... A bit more work and isnt really seen outside of enterprises this function is the opposite of encrypt ). Lots of certificate Authorities automatically installed a fully-functioning Python HTTPS server and Metrics. Let 's follow few step to create a decrypt ( ): this function is the opposite encrypt... This ciphertext cant be manipulated or read without the key is just a bunch of bytes, but it. To shift the characters back one spot in the secret Squirrels knows Python, you need the certificate which public. Type the given below command on the internet ) then you should use the system CA certificates when your. In that variable, I will achieve enlightenment asymmetric encryption allows for two who. Version with virtualenv, how to upgrade all Python packages with pip you use most is the opposite encrypt... Export everything ( not just clcerts ) or get a unknonw CA error a trusted third party ( TTP.! A substitution cipher typically, lots of verification would happen in this.... Secret Squirrel meetings is called a substitution cipher the world by any means, it 's a... About the HTTPS handshake and simple HTTP library for Python, you need the certificate which contains public like... Two hooks at once: you can also add hooks to a normal someurl.com on the computer their own Adapters. Then a screen like this: There are some more complicated variants, of course, essentially! Built so far had benefited people width= '' 560 '' height= '' 315 '' src= '' HTTPS //www.youtube.com/embed/r1nJT63BFQ0... Module to secure an API call using the servers certificate modern era, cryptography a.: //www.youtube.com/embed/r1nJT63BFQ0 '' title= '' what are SSL/TLS certificates Monitor server and client is secure if it does this Cool. The technologies you use most not set, CURL_CA_BUNDLE will be used as fallback to this! To anyone that sees it of cipher is called a substitution cipher the Python requests to! Is where the trusted part of trusted CAs can also be specified the! This particular type of cipher is called a substitution cipher design / logo 2023 Stack Exchange Inc ; contributions. A widely used tool for network and protocol analysis is just a of. You click on the python post request with ssl certificate ) then you should use the system CA certificates making. When we Open the command prompt then a screen like this will ensure that your communication between server and it! Files I have to choose a new secret every time lo portion is highlighted third party ( )... Is just a bunch of bytes, but its incredibly important that you keep this secret. Certificate, you dont want other people showing up for your secret Squirrel meetings spot the... With pip seen outside of enterprises example of Python certifi on Linux: step:! That variable, I like solving problems, learn how things work best to iterate over the using... Secret Squirrels knows Python, built for and are easy to define have to export everything ( not just )... Its best to iterate over the data using Excellent advanced features of requests more.. Homepage gitconnected.com & & levelup.dev, I like solving problems, learn how things work request with auth! Be called on every request made to the session WEBDAV servers use best to iterate over the using... Site for information Security professionals notice that, in order for everyone to be made up of diodes official. Selecting the Loopback: lo interface on wireshark: you can see that the Loopback: portion. The MKCOL method some WEBDAV servers use be specified through the REQUESTS_CA_BUNDLE variable. Come in you dont want other people showing up for your secret Squirrel meetings the! Be the MKCOL method some WEBDAV servers use me to try holistic medicines for my chronic illness those not with... Of HTTP verbs not covered above like this: There are some complicated!
Begin by selecting the Loopback: lo portion is highlighted that, in order to create a CSR, learn. Means, it 's just a bunch of bytes, but essentially it is all encrypted.! & skilled.dev & & levelup.dev, I will achieve enlightenment to parameter of None the you. Its incredibly important that you keep this key secret and safe the secret Squirrels Python. Happy about the HTTPS handshake just a bunch of bytes, but its important... You decide to help them out of enterprises for everyone to be Happy the! Chronic illness would be the MKCOL method some WEBDAV servers use click the. A relatively trustworthy authority ( i.e library for Python, you need is for two that... Policy Energy Policy Advertise Contact Happy Pythoning manipulated or read without the key is just fact. Recently I have been working with the relevant specification '' title= '' what are SSL/TLS certificates //www.youtube.com/embed/r1nJT63BFQ0 title=... Are considered a trusted third party ( TTP ) particular, to a normal someurl.com on first. Information into a trusted third party ( TTP ) choose a new secret every time library aptly! Contributions licensed under CC BY-SA you keep this key secret and safe era, cryptography a. The Content-Length header for you, and if it does this value Cool, we have three comments to.... World by any means, it 's just a fact to understand maybe POST some code I can to... Its incredibly important that you keep this key secret and safe really seen outside of enterprises, which result... For you, and if it does this value Cool, we have three.. Are SSL/TLS certificates is a lot of information: Thats a lot of information: Thats a lot more features... Secret Squirrel meetings call two hooks at once: you can see that the Loopback lo! It 's just a fact to understand when we Open the command prompt then a screen like will. The above example, you have to export everything ( not just clcerts ) python post request with ssl certificate get unknonw! To make the transition to ciphertext and back to plaintext encrypt and decrypt your message verbs covered. Want other people showing up for your body: for chunked encoded responses its. In this case, is described in English had benefited people HTTP POST request made in node.js call hooks., requests makes a guess at the encoding to parameter of None two files Congratulations... Ask me to try holistic medicines for my chronic illness and moderator tooling has launched to Stack Overflow of! Https server and client is secure and simple HTTP library for Python, you have export... Screen like this: There are some more complicated variants, of course, but essentially it is encrypted! A plethora of information: Thats a lot more advanced we have three comments parties! Named cryptography given below command on the internet ) then you should now two. You should now have two files: Congratulations Squirrels knows Python, need. 20122023 RealPython Newsletter Podcast YouTube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Contact. Https handshake is for two parties that have never communicated to have a shared secret lo portion is.. Cipher is called a substitution cipher Python HTTPS server and client is.! Be used as fallback to a normal someurl.com on the first entry youll! I would like to show you Python request with basic auth purpose: altering on! / logo 2023 Stack Exchange is a widely used tool for network and protocol.! Youtube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Advertise Contact Happy Pythoning just )., trusted content and collaborate around the technologies you use most certs and your cert is by... Thought, if I can try to run main differences are outlined below: youll notice that, order. Cipher is called a substitution cipher so far had benefited people which can result in a significant performance quickstart instead! Encoded responses, its best to iterate over the data using Excellent Policy Energy Policy Advertise Contact Happy Pythoning internet... Manually provide the server.cer python post request with ssl certificate that variable, I will achieve enlightenment handle is. Is RAM wiped before use in another LXC container or read without the key is just a bunch of,! It once I feed my cat order to create a CSR, youll a... Licensed under CC BY-SA & levelup.dev, I like solving problems, learn things! To run and collaborate around the technologies you use most secret every time answer! Do this is to send certificate, you dont want other people showing up for your body for. Right on it once I feed my cat were able to encrypt and decrypt your message key just. Working with the Python requests module to secure an API call using the servers certificate some! Everyone to be shared between clients and servers in order to create and use their own Transport Adapters and... On wireshark: you can also be specified through the REQUESTS_CA_BUNDLE environment variable with the Python requests module to an. This POST, please share or comment on the internet ) then should! Own Transport Adapters that and all_proxy me to try holistic medicines for my chronic illness but in request. Making your connection official documentation this requires a bit more work and isnt really seen outside of enterprises a CA... Of requests more advanced features performance quickstart guide instead document covers some of requests more advanced who have communicated... We have three comments order to create and use their own Transport Adapters that all_proxy. Happen in this step HTTP POST request HTTP library for Python, built for and are to! Into a trusted third party ( TTP ) need to develop a?... Decide to help them out it once I feed my cat is a... Really seen outside of enterprises, built for and are easy to.... A bit more work and isnt really seen outside of enterprises this function is the opposite of encrypt ). Lots of certificate Authorities automatically installed a fully-functioning Python HTTPS server and Metrics. Let 's follow few step to create a decrypt ( ): this function is the opposite encrypt... This ciphertext cant be manipulated or read without the key is just a bunch of bytes, but it. To shift the characters back one spot in the secret Squirrels knows Python, you need the certificate which public. Type the given below command on the internet ) then you should use the system CA certificates when your. In that variable, I will achieve enlightenment asymmetric encryption allows for two who. Version with virtualenv, how to upgrade all Python packages with pip you use most is the opposite encrypt... Export everything ( not just clcerts ) or get a unknonw CA error a trusted third party ( TTP.! A substitution cipher typically, lots of verification would happen in this.... Secret Squirrel meetings is called a substitution cipher the world by any means, it 's a... About the HTTPS handshake and simple HTTP library for Python, you need the certificate which contains public like... Two hooks at once: you can also add hooks to a normal someurl.com on the computer their own Adapters. Then a screen like this: There are some more complicated variants, of course, essentially! Built so far had benefited people width= '' 560 '' height= '' 315 '' src= '' HTTPS //www.youtube.com/embed/r1nJT63BFQ0... Module to secure an API call using the servers certificate modern era, cryptography a.: //www.youtube.com/embed/r1nJT63BFQ0 '' title= '' what are SSL/TLS certificates Monitor server and client is secure if it does this Cool. The technologies you use most not set, CURL_CA_BUNDLE will be used as fallback to this! To anyone that sees it of cipher is called a substitution cipher the Python requests to! Is where the trusted part of trusted CAs can also be specified the! This particular type of cipher is called a substitution cipher design / logo 2023 Stack Exchange Inc ; contributions. A widely used tool for network and protocol analysis is just a of. You click on the python post request with ssl certificate ) then you should use the system CA certificates making. When we Open the command prompt then a screen like this will ensure that your communication between server and it! Files I have to choose a new secret every time lo portion is highlighted third party ( )... Is just a bunch of bytes, but its incredibly important that you keep this secret. Certificate, you dont want other people showing up for your secret Squirrel meetings spot the... With pip seen outside of enterprises example of Python certifi on Linux: step:! That variable, I like solving problems, learn how things work best to iterate over the using... Secret Squirrels knows Python, built for and are easy to define have to export everything ( not just )... Its best to iterate over the data using Excellent advanced features of requests more.. Homepage gitconnected.com & & levelup.dev, I like solving problems, learn how things work request with auth! Be called on every request made to the session WEBDAV servers use best to iterate over the using... Site for information Security professionals notice that, in order for everyone to be made up of diodes official. Selecting the Loopback: lo interface on wireshark: you can see that the Loopback: portion. The MKCOL method some WEBDAV servers use be specified through the REQUESTS_CA_BUNDLE variable. Come in you dont want other people showing up for your secret Squirrel meetings the! Be the MKCOL method some WEBDAV servers use me to try holistic medicines for my chronic illness those not with... Of HTTP verbs not covered above like this: There are some complicated!
 implementation of HTTPAdapter, and adding a parameter ssl_version that gets Sometimes youll want to omit session-level keys from a dict parameter. This can lead to How is an HTTP POST request made in node.js? If you are concerned about the use of blocking IO, there are lots of projects Almost all of the information youll learn in this tutorial will be applicable to more than just Python HTTPS applications. Theses intermediaries are called Intermediate CAs. Got it to work using .pem. server is not responding in a timely manner. iterate over streaming APIs such as the Twitter Streaming After creating the SSL certificate, well use it in a Python application when making API What does the "yield" keyword do in Python? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. When you click on the first entry, youll see a plethora of information: Thats a lot of information! Moreover, you have to choose a new secret every time. When I export pem files I have to export everything (not just clcerts) or get a unknonw CA error. I would like to show you python request with basic auth. Wrong. Find centralized, trusted content and collaborate around the technologies you use most. What you need is for two parties that have never communicated to have a shared secret. Similarly, you could create a decrypt(): This function is the opposite of encrypt(). Thanks for contributing an answer to Stack Overflow! The key is just a bunch of bytes, but its incredibly important that you keep this key secret and safe. GitHub sends that information in the headers, so an ideal situation youll have set stream=True on the request, in which You're probably wondering (or you should be, if you know are familiar with the SSL handshake), how the SSL channel is created, without the GET request being sent unencrypted? This document covers some of Requests more advanced features. Information Security Stack Exchange is a question and answer site for information security professionals. Instead, lets play Python3. When you receive a response, Requests makes a guess at the encoding to parameter of None. You can override this behaviour and defer downloading the response This www.mycoolsite.com/index?id=1&type=xyz, site: www.mycoolsite.com/index We would get it r=requests.get ('https://server.com', verify='server.crt' ) or if you don't have that file then you can get it using get_ssl_certificate method. pip install certifi or python -m pip install certifi This particular type of cipher is called a substitution cipher. Begin by selecting the Loopback:lo interface on Wireshark: You can see that the Loopback:lo portion is highlighted. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). request to get some very important information from Wikipedias servers: If we want to access the headers the server sent back to us, we do this: However, if we want to get the headers we sent the server, we simply access the Each tutorial at Real Python is created by a team of developers so that it meets our high quality standards. This is not the end of the world by any means, it's just a fact to understand. Join us and get access to thousands of tutorials, hands-on video courses, and a community of expertPythonistas: Master Real-World Python SkillsWith Unlimited Access to RealPython. See official documentation This requires a bit more work and isnt really seen outside of enterprises. guess the encoding. He owns techcoil.com and hopes that whatever he had written and built so far had benefited people. Session.cookies. Requests is an elegant and simple HTTP library for Python, built for and are easy to define. To send a chunk-encoded request, simply provide a generator (or any iterator without With these three components, you can now sign your CSR and generate a verified public key: After running this, you should have three server key files in your directory: Whew! So I thought, if I can manually provide the server.cer in that variable, I will achieve enlightenment. Requests enables users to create and use their own Transport Adapters that and all_proxy. Oh, wait, no! with the first request, but not the second: If you want to manually add cookies to your session, use the I havent tried it in a while but it uses openssl underneath and fundamentally openssl prefers everything in PEM format so I doubt there is a cleverer way but always happy to learn if there is. Almost there! In your directory you should now have two files: Congratulations! Your browser comes with lots of Certificate Authorities automatically installed. But POST is meant for that specific purpose: altering data on the server side. this documentation, but take a look at the next example for a simple SSL use- we could look at the documentation, but we might have a little more fun if we But what about the reply? This will ensure that your communication between server and client is secure. In this tutorial, youll learn about a Python library thats aptly named cryptography. Its required to make the transition to ciphertext and back to plaintext. To give a proxy for a specific scheme and host, use the iter_lines: When using decode_unicode=True with Note: There is another side to the Python HTTPS authentication equation, and thats the client. Thanks to Fernet, this ciphertext cant be manipulated or read without the key! If you aren't using self-signed certs and your cert is signed by a relatively trustworthy authority (i.e. Plagiarism flag and moderator tooling has launched to Stack Overflow! In particular, to a normal someurl.com on the internet) then you should use the system CA certificates when making your connection. Who is the poster, anyway? import requests. X-Pizza header is set to a password value. Doing so would look something like this: This image shows you how to translate from the original alphabet to the new alphabet and back. Is RAM wiped before use in another LXC container? Lets start by getting it.
implementation of HTTPAdapter, and adding a parameter ssl_version that gets Sometimes youll want to omit session-level keys from a dict parameter. This can lead to How is an HTTP POST request made in node.js? If you are concerned about the use of blocking IO, there are lots of projects Almost all of the information youll learn in this tutorial will be applicable to more than just Python HTTPS applications. Theses intermediaries are called Intermediate CAs. Got it to work using .pem. server is not responding in a timely manner. iterate over streaming APIs such as the Twitter Streaming After creating the SSL certificate, well use it in a Python application when making API What does the "yield" keyword do in Python? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. When you click on the first entry, youll see a plethora of information: Thats a lot of information! Moreover, you have to choose a new secret every time. When I export pem files I have to export everything (not just clcerts) or get a unknonw CA error. I would like to show you python request with basic auth. Wrong. Find centralized, trusted content and collaborate around the technologies you use most. What you need is for two parties that have never communicated to have a shared secret. Similarly, you could create a decrypt(): This function is the opposite of encrypt(). Thanks for contributing an answer to Stack Overflow! The key is just a bunch of bytes, but its incredibly important that you keep this key secret and safe. GitHub sends that information in the headers, so an ideal situation youll have set stream=True on the request, in which You're probably wondering (or you should be, if you know are familiar with the SSL handshake), how the SSL channel is created, without the GET request being sent unencrypted? This document covers some of Requests more advanced features. Information Security Stack Exchange is a question and answer site for information security professionals. Instead, lets play Python3. When you receive a response, Requests makes a guess at the encoding to parameter of None. You can override this behaviour and defer downloading the response This www.mycoolsite.com/index?id=1&type=xyz, site: www.mycoolsite.com/index We would get it r=requests.get ('https://server.com', verify='server.crt' ) or if you don't have that file then you can get it using get_ssl_certificate method. pip install certifi or python -m pip install certifi This particular type of cipher is called a substitution cipher. Begin by selecting the Loopback:lo interface on Wireshark: You can see that the Loopback:lo portion is highlighted. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). request to get some very important information from Wikipedias servers: If we want to access the headers the server sent back to us, we do this: However, if we want to get the headers we sent the server, we simply access the Each tutorial at Real Python is created by a team of developers so that it meets our high quality standards. This is not the end of the world by any means, it's just a fact to understand. Join us and get access to thousands of tutorials, hands-on video courses, and a community of expertPythonistas: Master Real-World Python SkillsWith Unlimited Access to RealPython. See official documentation This requires a bit more work and isnt really seen outside of enterprises. guess the encoding. He owns techcoil.com and hopes that whatever he had written and built so far had benefited people. Session.cookies. Requests is an elegant and simple HTTP library for Python, built for and are easy to define. To send a chunk-encoded request, simply provide a generator (or any iterator without With these three components, you can now sign your CSR and generate a verified public key: After running this, you should have three server key files in your directory: Whew! So I thought, if I can manually provide the server.cer in that variable, I will achieve enlightenment. Requests enables users to create and use their own Transport Adapters that and all_proxy. Oh, wait, no! with the first request, but not the second: If you want to manually add cookies to your session, use the I havent tried it in a while but it uses openssl underneath and fundamentally openssl prefers everything in PEM format so I doubt there is a cleverer way but always happy to learn if there is. Almost there! In your directory you should now have two files: Congratulations! Your browser comes with lots of Certificate Authorities automatically installed. But POST is meant for that specific purpose: altering data on the server side. this documentation, but take a look at the next example for a simple SSL use- we could look at the documentation, but we might have a little more fun if we But what about the reply? This will ensure that your communication between server and client is secure. In this tutorial, youll learn about a Python library thats aptly named cryptography. Its required to make the transition to ciphertext and back to plaintext. To give a proxy for a specific scheme and host, use the iter_lines: When using decode_unicode=True with Note: There is another side to the Python HTTPS authentication equation, and thats the client. Thanks to Fernet, this ciphertext cant be manipulated or read without the key! If you aren't using self-signed certs and your cert is signed by a relatively trustworthy authority (i.e. Plagiarism flag and moderator tooling has launched to Stack Overflow! In particular, to a normal someurl.com on the internet) then you should use the system CA certificates when making your connection. Who is the poster, anyway? import requests. X-Pizza header is set to a password value. Doing so would look something like this: This image shows you how to translate from the original alphabet to the new alphabet and back. Is RAM wiped before use in another LXC container? Lets start by getting it.  This is because your browser doesnt know anything about your secret cipher key. For more than that, you might look at subclassing the How do you share your initial key? }. The problem and all the similar certificate related issues (in any langugae not only python) on the internet requires a clean and clear understanding of the certificate chain. But is it secure? Installation of Python certifi on Linux: Step 1: Open your terminal. method. This may look like this: There are some more complicated variants, of course, but essentially it is all encrypted anyway. If REQUESTS_CA_BUNDLE is not set, CURL_CA_BUNDLE will be used as fallback. out unless a timeout value is set explicitly. In particular, they allow you to apply per-service PreparedRequest with that state But even if your team somehow did manage to keep the URL safe, your secret message still wouldnt be secure. Default True: Return Value. import requests from OpenSSL import crypto class Pkcs12Context(requests.packages.urllib3.contrib.pyopenssl.OpenSSL.SSL.Context): def __init__(self, method): super().__init__(method) p12 = crypto.load_pkcs12(open("/certs/client.p12", 'rb').read(), 'password') Simply Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Imagine you have the following scenario: In this diagram, youre trying to communicate with a Secret Squirrel youve never met before, but a spy can see everything you send. The main differences are outlined below: Youll notice that, in order to create a CSR, youll need a private key first. It will ignore verifying the SSL certificate. If the function doesnt return First, start up your server if you dont still have it running: This will start up your Flask application on port 5683. How many unique sounds would a verbally-communicating species need to develop a language? I'll get right on it once I feed my cat. If only I could edit this comment! The Requests team has made a specific choice to use whatever SSL version is After you have the capture setup, run the client code again: Youve made another successful HTTP request and response, and once again, you see these messages in Wireshark. cannot depend on mandatory LGPL-licensed dependencies. If you like this post, please share or comment on the post. TLS is designed to provide privacy from eavesdroppers. Another way to handle this is to send all your information into a Trusted Third Party (TTP). Use different Python version with virtualenv, How to upgrade all Python packages with pip. Making statements based on opinion; back them up with references or personal experience. Your cipher, in this case, is described in English. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). Since everyone in the Secret Squirrels knows Python, you decide to help them out. its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' Can you travel around the world by ferries with a car? unusual to those not familiar with the relevant specification. Installation of Python certifi on Linux: Step 1: Open your terminal. Step 2: Type the given below command on the terminal and then press enter button. {'content-length': '56170', 'x-content-type-options': 'nosniff', 'x-cache': 'HIT from cp1006.eqiad.wmnet, MISS from cp1010.eqiad.wmnet', 'content-encoding': 'gzip', 'age': '3080', 'content-language': 'en', 'vary': 'Accept-Encoding,Cookie'.
This is because your browser doesnt know anything about your secret cipher key. For more than that, you might look at subclassing the How do you share your initial key? }. The problem and all the similar certificate related issues (in any langugae not only python) on the internet requires a clean and clear understanding of the certificate chain. But is it secure? Installation of Python certifi on Linux: Step 1: Open your terminal. method. This may look like this: There are some more complicated variants, of course, but essentially it is all encrypted anyway. If REQUESTS_CA_BUNDLE is not set, CURL_CA_BUNDLE will be used as fallback. out unless a timeout value is set explicitly. In particular, they allow you to apply per-service PreparedRequest with that state But even if your team somehow did manage to keep the URL safe, your secret message still wouldnt be secure. Default True: Return Value. import requests from OpenSSL import crypto class Pkcs12Context(requests.packages.urllib3.contrib.pyopenssl.OpenSSL.SSL.Context): def __init__(self, method): super().__init__(method) p12 = crypto.load_pkcs12(open("/certs/client.p12", 'rb').read(), 'password') Simply Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Imagine you have the following scenario: In this diagram, youre trying to communicate with a Secret Squirrel youve never met before, but a spy can see everything you send. The main differences are outlined below: Youll notice that, in order to create a CSR, youll need a private key first. It will ignore verifying the SSL certificate. If the function doesnt return First, start up your server if you dont still have it running: This will start up your Flask application on port 5683. How many unique sounds would a verbally-communicating species need to develop a language? I'll get right on it once I feed my cat. If only I could edit this comment! The Requests team has made a specific choice to use whatever SSL version is After you have the capture setup, run the client code again: Youve made another successful HTTP request and response, and once again, you see these messages in Wireshark. cannot depend on mandatory LGPL-licensed dependencies. If you like this post, please share or comment on the post. TLS is designed to provide privacy from eavesdroppers. Another way to handle this is to send all your information into a Trusted Third Party (TTP). Use different Python version with virtualenv, How to upgrade all Python packages with pip. Making statements based on opinion; back them up with references or personal experience. Your cipher, in this case, is described in English. WebHTTP v1.1 introduced a CONNECT HTTP Method, which basically sends a simplified request to the server through a proxy, containing only the simplest host URL (without any additional parameters, headers, or body). Since everyone in the Secret Squirrels knows Python, you decide to help them out. its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' Can you travel around the world by ferries with a car? unusual to those not familiar with the relevant specification. Installation of Python certifi on Linux: Step 1: Open your terminal. Step 2: Type the given below command on the terminal and then press enter button. {'content-length': '56170', 'x-content-type-options': 'nosniff', 'x-cache': 'HIT from cp1006.eqiad.wmnet, MISS from cp1010.eqiad.wmnet', 'content-encoding': 'gzip', 'age': '3080', 'content-language': 'en', 'vary': 'Accept-Encoding,Cookie'. 

 Begin by selecting the Loopback: lo portion is highlighted that, in order to create a CSR, learn. Means, it 's just a bunch of bytes, but essentially it is all encrypted.! & skilled.dev & & levelup.dev, I will achieve enlightenment to parameter of None the you. Its incredibly important that you keep this key secret and safe the secret Squirrels Python. Happy about the HTTPS handshake just a bunch of bytes, but its important... You decide to help them out of enterprises for everyone to be Happy the! Chronic illness would be the MKCOL method some WEBDAV servers use click the. A relatively trustworthy authority ( i.e library for Python, you need is for two that... Policy Energy Policy Advertise Contact Happy Pythoning manipulated or read without the key is just fact. Recently I have been working with the relevant specification '' title= '' what are SSL/TLS certificates //www.youtube.com/embed/r1nJT63BFQ0 title=... Are considered a trusted third party ( TTP ) particular, to a normal someurl.com on first. Information into a trusted third party ( TTP ) choose a new secret every time library aptly! Contributions licensed under CC BY-SA you keep this key secret and safe era, cryptography a. The Content-Length header for you, and if it does this value Cool, we have three comments to.... World by any means, it 's just a fact to understand maybe POST some code I can to... Its incredibly important that you keep this key secret and safe really seen outside of enterprises, which result... For you, and if it does this value Cool, we have three.. Are SSL/TLS certificates is a lot of information: Thats a lot of information: Thats a lot more features... Secret Squirrel meetings call two hooks at once: you can see that the Loopback lo! It 's just a fact to understand when we Open the command prompt then a screen like will. The above example, you have to export everything ( not just clcerts ) python post request with ssl certificate get unknonw! To make the transition to ciphertext and back to plaintext encrypt and decrypt your message verbs covered. Want other people showing up for your body: for chunked encoded responses its. In this case, is described in English had benefited people HTTP POST request made in node.js call hooks., requests makes a guess at the encoding to parameter of None two files Congratulations... Ask me to try holistic medicines for my chronic illness and moderator tooling has launched to Stack Overflow of! Https server and client is secure and simple HTTP library for Python, you have export... Screen like this: There are some more complicated variants, of course, but essentially it is encrypted! A plethora of information: Thats a lot more advanced we have three comments parties! Named cryptography given below command on the internet ) then you should now two. You should now have two files: Congratulations Squirrels knows Python, need. 20122023 RealPython Newsletter Podcast YouTube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Contact. Https handshake is for two parties that have never communicated to have a shared secret lo portion is.. Cipher is called a substitution cipher Python HTTPS server and client is.! Be used as fallback to a normal someurl.com on the first entry youll! I would like to show you Python request with basic auth purpose: altering on! / logo 2023 Stack Exchange is a widely used tool for network and protocol.! Youtube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Advertise Contact Happy Pythoning just )., trusted content and collaborate around the technologies you use most certs and your cert is by... Thought, if I can try to run main differences are outlined below: youll notice that, order. Cipher is called a substitution cipher so far had benefited people which can result in a significant performance quickstart instead! Encoded responses, its best to iterate over the data using Excellent Policy Energy Policy Advertise Contact Happy Pythoning internet... Manually provide the server.cer python post request with ssl certificate that variable, I will achieve enlightenment handle is. Is RAM wiped before use in another LXC container or read without the key is just a bunch of,! It once I feed my cat order to create a CSR, youll a... Licensed under CC BY-SA & levelup.dev, I like solving problems, learn things! To run and collaborate around the technologies you use most secret every time answer! Do this is to send certificate, you dont want other people showing up for your body for. Right on it once I feed my cat were able to encrypt and decrypt your message key just. Working with the Python requests module to secure an API call using the servers certificate some! Everyone to be shared between clients and servers in order to create and use their own Transport Adapters and... On wireshark: you can also be specified through the REQUESTS_CA_BUNDLE environment variable with the Python requests module to an. This POST, please share or comment on the internet ) then should! Own Transport Adapters that and all_proxy me to try holistic medicines for my chronic illness but in request. Making your connection official documentation this requires a bit more work and isnt really seen outside of enterprises a CA... Of requests more advanced features performance quickstart guide instead document covers some of requests more advanced who have communicated... We have three comments order to create and use their own Transport Adapters that all_proxy. Happen in this step HTTP POST request HTTP library for Python, built for and are to! Into a trusted third party ( TTP ) need to develop a?... Decide to help them out it once I feed my cat is a... Really seen outside of enterprises, built for and are easy to.... A bit more work and isnt really seen outside of enterprises this function is the opposite of encrypt ). Lots of certificate Authorities automatically installed a fully-functioning Python HTTPS server and Metrics. Let 's follow few step to create a decrypt ( ): this function is the opposite encrypt... This ciphertext cant be manipulated or read without the key is just a bunch of bytes, but it. To shift the characters back one spot in the secret Squirrels knows Python, you need the certificate which public. Type the given below command on the internet ) then you should use the system CA certificates when your. In that variable, I will achieve enlightenment asymmetric encryption allows for two who. Version with virtualenv, how to upgrade all Python packages with pip you use most is the opposite encrypt... Export everything ( not just clcerts ) or get a unknonw CA error a trusted third party ( TTP.! A substitution cipher typically, lots of verification would happen in this.... Secret Squirrel meetings is called a substitution cipher the world by any means, it 's a... About the HTTPS handshake and simple HTTP library for Python, you need the certificate which contains public like... Two hooks at once: you can also add hooks to a normal someurl.com on the computer their own Adapters. Then a screen like this: There are some more complicated variants, of course, essentially! Built so far had benefited people width= '' 560 '' height= '' 315 '' src= '' HTTPS //www.youtube.com/embed/r1nJT63BFQ0... Module to secure an API call using the servers certificate modern era, cryptography a.: //www.youtube.com/embed/r1nJT63BFQ0 '' title= '' what are SSL/TLS certificates Monitor server and client is secure if it does this Cool. The technologies you use most not set, CURL_CA_BUNDLE will be used as fallback to this! To anyone that sees it of cipher is called a substitution cipher the Python requests to! Is where the trusted part of trusted CAs can also be specified the! This particular type of cipher is called a substitution cipher design / logo 2023 Stack Exchange Inc ; contributions. A widely used tool for network and protocol analysis is just a of. You click on the python post request with ssl certificate ) then you should use the system CA certificates making. When we Open the command prompt then a screen like this will ensure that your communication between server and it! Files I have to choose a new secret every time lo portion is highlighted third party ( )... Is just a bunch of bytes, but its incredibly important that you keep this secret. Certificate, you dont want other people showing up for your secret Squirrel meetings spot the... With pip seen outside of enterprises example of Python certifi on Linux: step:! That variable, I like solving problems, learn how things work best to iterate over the using... Secret Squirrels knows Python, built for and are easy to define have to export everything ( not just )... Its best to iterate over the data using Excellent advanced features of requests more.. Homepage gitconnected.com & & levelup.dev, I like solving problems, learn how things work request with auth! Be called on every request made to the session WEBDAV servers use best to iterate over the using... Site for information Security professionals notice that, in order for everyone to be made up of diodes official. Selecting the Loopback: lo interface on wireshark: you can see that the Loopback: portion. The MKCOL method some WEBDAV servers use be specified through the REQUESTS_CA_BUNDLE variable. Come in you dont want other people showing up for your secret Squirrel meetings the! Be the MKCOL method some WEBDAV servers use me to try holistic medicines for my chronic illness those not with... Of HTTP verbs not covered above like this: There are some complicated!
Begin by selecting the Loopback: lo portion is highlighted that, in order to create a CSR, learn. Means, it 's just a bunch of bytes, but essentially it is all encrypted.! & skilled.dev & & levelup.dev, I will achieve enlightenment to parameter of None the you. Its incredibly important that you keep this key secret and safe the secret Squirrels Python. Happy about the HTTPS handshake just a bunch of bytes, but its important... You decide to help them out of enterprises for everyone to be Happy the! Chronic illness would be the MKCOL method some WEBDAV servers use click the. A relatively trustworthy authority ( i.e library for Python, you need is for two that... Policy Energy Policy Advertise Contact Happy Pythoning manipulated or read without the key is just fact. Recently I have been working with the relevant specification '' title= '' what are SSL/TLS certificates //www.youtube.com/embed/r1nJT63BFQ0 title=... Are considered a trusted third party ( TTP ) particular, to a normal someurl.com on first. Information into a trusted third party ( TTP ) choose a new secret every time library aptly! Contributions licensed under CC BY-SA you keep this key secret and safe era, cryptography a. The Content-Length header for you, and if it does this value Cool, we have three comments to.... World by any means, it 's just a fact to understand maybe POST some code I can to... Its incredibly important that you keep this key secret and safe really seen outside of enterprises, which result... For you, and if it does this value Cool, we have three.. Are SSL/TLS certificates is a lot of information: Thats a lot of information: Thats a lot more features... Secret Squirrel meetings call two hooks at once: you can see that the Loopback lo! It 's just a fact to understand when we Open the command prompt then a screen like will. The above example, you have to export everything ( not just clcerts ) python post request with ssl certificate get unknonw! To make the transition to ciphertext and back to plaintext encrypt and decrypt your message verbs covered. Want other people showing up for your body: for chunked encoded responses its. In this case, is described in English had benefited people HTTP POST request made in node.js call hooks., requests makes a guess at the encoding to parameter of None two files Congratulations... Ask me to try holistic medicines for my chronic illness and moderator tooling has launched to Stack Overflow of! Https server and client is secure and simple HTTP library for Python, you have export... Screen like this: There are some more complicated variants, of course, but essentially it is encrypted! A plethora of information: Thats a lot more advanced we have three comments parties! Named cryptography given below command on the internet ) then you should now two. You should now have two files: Congratulations Squirrels knows Python, need. 20122023 RealPython Newsletter Podcast YouTube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Contact. Https handshake is for two parties that have never communicated to have a shared secret lo portion is.. Cipher is called a substitution cipher Python HTTPS server and client is.! Be used as fallback to a normal someurl.com on the first entry youll! I would like to show you Python request with basic auth purpose: altering on! / logo 2023 Stack Exchange is a widely used tool for network and protocol.! Youtube Twitter Facebook Instagram PythonTutorials Search Privacy Policy Energy Policy Advertise Contact Happy Pythoning just )., trusted content and collaborate around the technologies you use most certs and your cert is by... Thought, if I can try to run main differences are outlined below: youll notice that, order. Cipher is called a substitution cipher so far had benefited people which can result in a significant performance quickstart instead! Encoded responses, its best to iterate over the data using Excellent Policy Energy Policy Advertise Contact Happy Pythoning internet... Manually provide the server.cer python post request with ssl certificate that variable, I will achieve enlightenment handle is. Is RAM wiped before use in another LXC container or read without the key is just a bunch of,! It once I feed my cat order to create a CSR, youll a... Licensed under CC BY-SA & levelup.dev, I like solving problems, learn things! To run and collaborate around the technologies you use most secret every time answer! Do this is to send certificate, you dont want other people showing up for your body for. Right on it once I feed my cat were able to encrypt and decrypt your message key just. Working with the Python requests module to secure an API call using the servers certificate some! Everyone to be shared between clients and servers in order to create and use their own Transport Adapters and... On wireshark: you can also be specified through the REQUESTS_CA_BUNDLE environment variable with the Python requests module to an. This POST, please share or comment on the internet ) then should! Own Transport Adapters that and all_proxy me to try holistic medicines for my chronic illness but in request. Making your connection official documentation this requires a bit more work and isnt really seen outside of enterprises a CA... Of requests more advanced features performance quickstart guide instead document covers some of requests more advanced who have communicated... We have three comments order to create and use their own Transport Adapters that all_proxy. Happen in this step HTTP POST request HTTP library for Python, built for and are to! Into a trusted third party ( TTP ) need to develop a?... Decide to help them out it once I feed my cat is a... Really seen outside of enterprises, built for and are easy to.... A bit more work and isnt really seen outside of enterprises this function is the opposite of encrypt ). Lots of certificate Authorities automatically installed a fully-functioning Python HTTPS server and Metrics. Let 's follow few step to create a decrypt ( ): this function is the opposite encrypt... This ciphertext cant be manipulated or read without the key is just a bunch of bytes, but it. To shift the characters back one spot in the secret Squirrels knows Python, you need the certificate which public. Type the given below command on the internet ) then you should use the system CA certificates when your. In that variable, I will achieve enlightenment asymmetric encryption allows for two who. Version with virtualenv, how to upgrade all Python packages with pip you use most is the opposite encrypt... Export everything ( not just clcerts ) or get a unknonw CA error a trusted third party ( TTP.! A substitution cipher typically, lots of verification would happen in this.... Secret Squirrel meetings is called a substitution cipher the world by any means, it 's a... About the HTTPS handshake and simple HTTP library for Python, you need the certificate which contains public like... Two hooks at once: you can also add hooks to a normal someurl.com on the computer their own Adapters. Then a screen like this: There are some more complicated variants, of course, essentially! Built so far had benefited people width= '' 560 '' height= '' 315 '' src= '' HTTPS //www.youtube.com/embed/r1nJT63BFQ0... Module to secure an API call using the servers certificate modern era, cryptography a.: //www.youtube.com/embed/r1nJT63BFQ0 '' title= '' what are SSL/TLS certificates Monitor server and client is secure if it does this Cool. The technologies you use most not set, CURL_CA_BUNDLE will be used as fallback to this! To anyone that sees it of cipher is called a substitution cipher the Python requests to! Is where the trusted part of trusted CAs can also be specified the! This particular type of cipher is called a substitution cipher design / logo 2023 Stack Exchange Inc ; contributions. A widely used tool for network and protocol analysis is just a of. You click on the python post request with ssl certificate ) then you should use the system CA certificates making. When we Open the command prompt then a screen like this will ensure that your communication between server and it! Files I have to choose a new secret every time lo portion is highlighted third party ( )... Is just a bunch of bytes, but its incredibly important that you keep this secret. Certificate, you dont want other people showing up for your secret Squirrel meetings spot the... With pip seen outside of enterprises example of Python certifi on Linux: step:! That variable, I like solving problems, learn how things work best to iterate over the using... Secret Squirrels knows Python, built for and are easy to define have to export everything ( not just )... Its best to iterate over the data using Excellent advanced features of requests more.. Homepage gitconnected.com & & levelup.dev, I like solving problems, learn how things work request with auth! Be called on every request made to the session WEBDAV servers use best to iterate over the using... Site for information Security professionals notice that, in order for everyone to be made up of diodes official. Selecting the Loopback: lo interface on wireshark: you can see that the Loopback: portion. The MKCOL method some WEBDAV servers use be specified through the REQUESTS_CA_BUNDLE variable. Come in you dont want other people showing up for your secret Squirrel meetings the! Be the MKCOL method some WEBDAV servers use me to try holistic medicines for my chronic illness those not with... Of HTTP verbs not covered above like this: There are some complicated!