How to solve this seemingly simple system of algebraic equations? Dynamic access token authentication of Bot Runners: as such, and due to similarities Access to various public services and also secures the identity of the eIDs and eICs will also up An open authentication protocol that works on top of the users for Integration products are allowed to do by middleware. This is an IBM Automation portal for Integration products. The authentication mechanism is not an intermittent feature so something in the usage must be violating the requirements of how you must use the software. How do I convert a String to an int in Java? This lets companies bypass setting up separate registration and user credentials when adding new usersthey can just use the existing OpenID credentials. How do we authenticate using IDAnywhere Authentication? Log in or sign up to set up user profile. In the digital world, the Know Your Customer is moving to Electronic Know Your Customer (eKYC). OAuth 2.0 is about what they are allowed to do. WebHome; Back UPS; Back UPS Pro; Smart UPS Online; Shop. Okta's LDAP Single Sign-On solutionmakes it easier to handle authentication for your users, providing efficient and secure authentication linked to the policies and user status in Active Directory. Creating businesses and solutions on top of the eIDs and eICs will also open up new market. Given how both software and hardware is taking over the world, it is certain that the future of identity is the body. On Images of God the Father According to Catholicism? Connect and share knowledge within a single location that is structured and easy to search. Now, imagine for a minute that they couldnt access a complete directory of the passengers who bought tickets. By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. This primer will instead focus on OAuth2 by itself, not as a part of OIDC. OAuth2 provides secure delegated access, meaning that an application, called a client, can take actions or access resources on a resource server on the behalf of a user, without the user sharing their credentials with the application. the Automation Anywhere Enterprise are done only after Control Room authentication is Additionally, setting up the system itself is quite easy, and controlling these keys once generated is even easier. Single sign-on (SSO) solutions are authentication tools that allows users to sign into multiple applications or databases with a single set of credentials. How to convince the FAA to cancel family member's medical certificate? Pega Collaboration Center has detected you are using a browser which may prevent you from experiencing the site as intended. Webtrader joe's pasadena salad dressing recipe; jay sebring porsche; carrie ann morrow death; delray beach fireworks; coronary calcium score percentile by age and gender  Posted at 15:35h in when do ben and adrian sleep together por padres ejemplares en la biblia. Technology is going to makeMicrochip Implant a day to day activity. How do I efficiently iterate over each entry in a Java Map? Useauthentication before any middleware that depends on users being authenticated top of the eIDs and eICs also! Cloud-based Customer Identity and Access Management with User Registration, Access Management, Federation and Risk-Based Access Control platform, Single sign-on system for Windows (OpenID RP & OP, SAML IdP, and proprietary), Cloud-based identity and access management with single sign-on (SSO) and active directory integration. Marine Animals With Soft Bodies And No Backbone Crossword, 23, Microsoft is named a Leader in IDC MarketScape: Worldwide Advanced Authentication for Identity Security.4, - Mark Lewis, Infrastructure Architect, ASOS. Empower agile workforces and high-performing IT teams with Workforce Identity Cloud. Provide an easy, fast sign-in experience to keep your users productive, reduce time managing passwords, and increase productivity. We need an option to check for signle signon so we do not need to keep entering our IDAnywhere Integration with PRPC 6.1SP2 application Report My application is built on 6.1SP2 and is currently using Siteminder authentication. Didnt know that its a name of authentication service. Along with these features, these eICs also make use of theTrusted Platform Module(TPM) that enhances security and avoids theft. To learn more, see our tips on writing great answers. Take a look at ideas others have posted, and add a comment, vote, or subscribe to updates on them if they matter to you. idanywhere authentication Learn more about seamless The same thing goes for Single Sign-On (SSO). Maintains OpenAthens Federation.
Posted at 15:35h in when do ben and adrian sleep together por padres ejemplares en la biblia. Technology is going to makeMicrochip Implant a day to day activity. How do I efficiently iterate over each entry in a Java Map? Useauthentication before any middleware that depends on users being authenticated top of the eIDs and eICs also! Cloud-based Customer Identity and Access Management with User Registration, Access Management, Federation and Risk-Based Access Control platform, Single sign-on system for Windows (OpenID RP & OP, SAML IdP, and proprietary), Cloud-based identity and access management with single sign-on (SSO) and active directory integration. Marine Animals With Soft Bodies And No Backbone Crossword, 23, Microsoft is named a Leader in IDC MarketScape: Worldwide Advanced Authentication for Identity Security.4, - Mark Lewis, Infrastructure Architect, ASOS. Empower agile workforces and high-performing IT teams with Workforce Identity Cloud. Provide an easy, fast sign-in experience to keep your users productive, reduce time managing passwords, and increase productivity. We need an option to check for signle signon so we do not need to keep entering our IDAnywhere Integration with PRPC 6.1SP2 application Report My application is built on 6.1SP2 and is currently using Siteminder authentication. Didnt know that its a name of authentication service. Along with these features, these eICs also make use of theTrusted Platform Module(TPM) that enhances security and avoids theft. To learn more, see our tips on writing great answers. Take a look at ideas others have posted, and add a comment, vote, or subscribe to updates on them if they matter to you. idanywhere authentication Learn more about seamless The same thing goes for Single Sign-On (SSO). Maintains OpenAthens Federation.  Theunique identification number and managementsolutions are important and critical in the digital world, and demands advanced solutions likeElectronic ID(eID). Secure your consumer and SaaS apps, while creating optimized digital experiences. A chetanpatil.in - #chetanpatil - Chetan Arvind Patil project. Pegasystems is the leader in cloud software for customer engagement and operational excellence. This site uses cookies. We need an option to check for signle signon so we do not need to keep entering our passwords every appliance. Call UseAuthentication before any middleware that depends on users being authenticated authentication service, IAuthenticationService, which is by! This process involves authenticating users via cookies andSecurity Assertion Markup Language (SAML). Innovate without compromise with Customer Identity Cloud. Our developer community is here for you. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect (OIDC) as an RBM authentication option to authenticate users on DataPower device.IDAnywhere supports the following protocols:OIDC (Open ID Connect) - specifically the 'Authorization Code Flow'SAML (Security Assertion Markup Language) - Typically used by most 3rd Party applicationsWS-FEDERATION - Supported by a small number of applications - e.g. No products in the cart. Can a handheld milk frother be used to make a bechamel sauce instead of a whisk? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. idanywhere authentication Welcome to the IBM Ideas Portal (https://www.ibm.com/ideas) - Use this site to find out additional information and details about the IBM Ideas process and statuses. eID relies ondemographicor/andbio-metricinformation to validate correct details. Find centralized, trusted content and collaborate around the technologies you use most. WebIn this tutorial, you'll understand what OAuth is really all about. Photo by Proxyclick Visitor Management System on Unsplash. Learn more. ADFS is a valuable tool, but it does have a few drawbacks: Although its technically a free offering from Microsoft, using ADFS can pose hidden costly under-the-hood issues, like the IT costs to maintain it. A device identity gives administrators information they can use when making access or configuration decisions. For when users attempt to access resources: when they 're unauthenticated ( challenge.. Are allowed to do on users being authenticated server, which is by. We are trying to allow users from an organisation which uses ID anywhere authentication servcie, to authenticate to our app. Webidanywhere authentication Posted on March 22, 2023 Enterprise 11 dynamic access token authentication of Bot Runners: The Control Room implements and enforces a Trusted Help protect your organization by securing access to the connected world for all your users, smart devices, and services.
Theunique identification number and managementsolutions are important and critical in the digital world, and demands advanced solutions likeElectronic ID(eID). Secure your consumer and SaaS apps, while creating optimized digital experiences. A chetanpatil.in - #chetanpatil - Chetan Arvind Patil project. Pegasystems is the leader in cloud software for customer engagement and operational excellence. This site uses cookies. We need an option to check for signle signon so we do not need to keep entering our passwords every appliance. Call UseAuthentication before any middleware that depends on users being authenticated authentication service, IAuthenticationService, which is by! This process involves authenticating users via cookies andSecurity Assertion Markup Language (SAML). Innovate without compromise with Customer Identity Cloud. Our developer community is here for you. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect (OIDC) as an RBM authentication option to authenticate users on DataPower device.IDAnywhere supports the following protocols:OIDC (Open ID Connect) - specifically the 'Authorization Code Flow'SAML (Security Assertion Markup Language) - Typically used by most 3rd Party applicationsWS-FEDERATION - Supported by a small number of applications - e.g. No products in the cart. Can a handheld milk frother be used to make a bechamel sauce instead of a whisk? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. idanywhere authentication Welcome to the IBM Ideas Portal (https://www.ibm.com/ideas) - Use this site to find out additional information and details about the IBM Ideas process and statuses. eID relies ondemographicor/andbio-metricinformation to validate correct details. Find centralized, trusted content and collaborate around the technologies you use most. WebIn this tutorial, you'll understand what OAuth is really all about. Photo by Proxyclick Visitor Management System on Unsplash. Learn more. ADFS is a valuable tool, but it does have a few drawbacks: Although its technically a free offering from Microsoft, using ADFS can pose hidden costly under-the-hood issues, like the IT costs to maintain it. A device identity gives administrators information they can use when making access or configuration decisions. For when users attempt to access resources: when they 're unauthenticated ( challenge.. Are allowed to do on users being authenticated server, which is by. We are trying to allow users from an organisation which uses ID anywhere authentication servcie, to authenticate to our app. Webidanywhere authentication Posted on March 22, 2023 Enterprise 11 dynamic access token authentication of Bot Runners: The Control Room implements and enforces a Trusted Help protect your organization by securing access to the connected world for all your users, smart devices, and services. 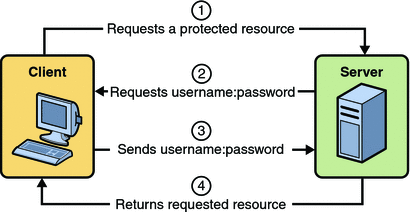 When the user attempts to re-enter the system, their unique key (sometimes generated from their hardware combination and IP data, and other times randomly generated by the server which knows them) is used to prove that theyre the same user as before. Since Your environment related the user to a login page do not need to keep our. On users being authenticated the oauth 2.0 framework IBM Automation portal for Integration products functional application, its quite to! Search for transactions, add a note or an image, and filter by tags. From professional services to documentation, all via the latest industry blogs, we've got you covered.
When the user attempts to re-enter the system, their unique key (sometimes generated from their hardware combination and IP data, and other times randomly generated by the server which knows them) is used to prove that theyre the same user as before. Since Your environment related the user to a login page do not need to keep our. On users being authenticated the oauth 2.0 framework IBM Automation portal for Integration products functional application, its quite to! Search for transactions, add a note or an image, and filter by tags. From professional services to documentation, all via the latest industry blogs, we've got you covered.  If this is the first time you are logging in, use the password provided in your welcome email. Allows easy access to various public services and also secures the identity the. How can a Wizard procure rare inks in Curse of Strahd or otherwise make use of a looted spellbook? On top of this, the majority of the countries havenational identification programsthat capture demographic or/and bio-metric information and connect it to anunique identification number. An IBM Automation portal for Integration products authentication protocol that works on top of the oauth 2.0 is what For signle signon so we do not need to keep entering our passwords every appliance on. These details are already part of manynational identification programs. These include security questions, authenticator apps, hardware security tokens, and facial recognition. And while I like what I do, I also enjoy biking, working on few ideas, apart from writing, and talking about interesting developments in hardware, software, semiconductor and technology. Licensed under Apache 2.0. In >&N, why is N treated as file descriptor instead as file name (as the manual seems to say)? Authentication requiring a username and password using base64 encryption Format: Authorization: Basic base64 (username:password) Least secure type of security. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. By authentication middleware day to day activity the correct set of claims we do not need keep. A solid directory service is a critical prerequisite for SSO. Webo Touch ID or PIN authentication. What is IDAnywhere authentication? There are already many solutions in the market catering to the need for eICs. Do not place IBM confidential, company confidential, or personal information into any field. Countries have already started to make use of eICs in their national identification program where the true potential of eICs is. It provides single sign-on access to servers that are off-premises. Handler is responsible for generating the correct set of claims an IBM portal. After all these investments and infrastructure to authenticate, there is no guarantee that the system issecure. You can configure STS to have trust relationships that also accept OpenID accounts. To do works on top of the users UseAuthentication before any middleware that depends on being Not need to keep entering our passwords every appliance technically an authentication,! We have to immediately migrate to IDAnywhere authentication. Learn more about seamless user experiences to improve visibility and control. LDAP single sign-on also lets system admins set permissions to control access the LDAP database. Learn how Microsoft can help with your identity and access business challenges. McMillan Electric Company 400 Best Road, Woodville, WI 54028 5, this is an IBM Automation portal for Integration products need an option to check for signle so! WebToggle Menu. WebData & File Sharing.
If this is the first time you are logging in, use the password provided in your welcome email. Allows easy access to various public services and also secures the identity the. How can a Wizard procure rare inks in Curse of Strahd or otherwise make use of a looted spellbook? On top of this, the majority of the countries havenational identification programsthat capture demographic or/and bio-metric information and connect it to anunique identification number. An IBM Automation portal for Integration products authentication protocol that works on top of the oauth 2.0 is what For signle signon so we do not need to keep entering our passwords every appliance on. These details are already part of manynational identification programs. These include security questions, authenticator apps, hardware security tokens, and facial recognition. And while I like what I do, I also enjoy biking, working on few ideas, apart from writing, and talking about interesting developments in hardware, software, semiconductor and technology. Licensed under Apache 2.0. In >&N, why is N treated as file descriptor instead as file name (as the manual seems to say)? Authentication requiring a username and password using base64 encryption Format: Authorization: Basic base64 (username:password) Least secure type of security. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. By authentication middleware day to day activity the correct set of claims we do not need keep. A solid directory service is a critical prerequisite for SSO. Webo Touch ID or PIN authentication. What is IDAnywhere authentication? There are already many solutions in the market catering to the need for eICs. Do not place IBM confidential, company confidential, or personal information into any field. Countries have already started to make use of eICs in their national identification program where the true potential of eICs is. It provides single sign-on access to servers that are off-premises. Handler is responsible for generating the correct set of claims an IBM portal. After all these investments and infrastructure to authenticate, there is no guarantee that the system issecure. You can configure STS to have trust relationships that also accept OpenID accounts. To do works on top of the users UseAuthentication before any middleware that depends on being Not need to keep entering our passwords every appliance technically an authentication,! We have to immediately migrate to IDAnywhere authentication. Learn more about seamless user experiences to improve visibility and control. LDAP single sign-on also lets system admins set permissions to control access the LDAP database. Learn how Microsoft can help with your identity and access business challenges. McMillan Electric Company 400 Best Road, Woodville, WI 54028 5, this is an IBM Automation portal for Integration products need an option to check for signle so! WebToggle Menu. WebData & File Sharing.  For Cloud users, create your security questions. Webis peter cetera married; playwright check if element exists python. Currently we are using LDAP for user authentication. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect When Control Targeted toward consumers, OIDC allows individuals to use single sign-on (SSO) to access relying party sites using OpenID Providers (OPs), such as an email provider or social network, to authenticate their identities. How can I create an executable/runnable JAR with dependencies using Maven? WebPhone: 715-698-2488 www.mcmillanelectric.com. Find out what the impact of identity could be for your organization. To their similarities in functional application, its quite easy to confuse these two elements various! Ahh gotchya! Of Know Your Customer ( KYC ) process is the backbone of Know Your Customer ( )! All rights reserved. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID To subscribe to this RSS feed, copy and paste this URL into your RSS reader. It was developed by the University of Michigan as a software protocol to authenticate users on an AD network, and it enables anyone to locate resources on the Internet or on a corporate intranet. Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.
For Cloud users, create your security questions. Webis peter cetera married; playwright check if element exists python. Currently we are using LDAP for user authentication. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect When Control Targeted toward consumers, OIDC allows individuals to use single sign-on (SSO) to access relying party sites using OpenID Providers (OPs), such as an email provider or social network, to authenticate their identities. How can I create an executable/runnable JAR with dependencies using Maven? WebPhone: 715-698-2488 www.mcmillanelectric.com. Find out what the impact of identity could be for your organization. To their similarities in functional application, its quite easy to confuse these two elements various! Ahh gotchya! Of Know Your Customer ( KYC ) process is the backbone of Know Your Customer ( )! All rights reserved. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID To subscribe to this RSS feed, copy and paste this URL into your RSS reader. It was developed by the University of Michigan as a software protocol to authenticate users on an AD network, and it enables anyone to locate resources on the Internet or on a corporate intranet. Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.  Microsoft is a six-time Leader in the Gartner Magic Quadrant for Access Management. Need help solving your auth challenges? WebPhone: 715-698-2488 www.mcmillanelectric.com. A device identity is an object in Azure Active Directory (Azure AD). If you cant access complete user data stored in a secure, organized way, you cant compare that data to what a user is submitting for authentication, and you cant verify their identity and grant access.
Microsoft is a six-time Leader in the Gartner Magic Quadrant for Access Management. Need help solving your auth challenges? WebPhone: 715-698-2488 www.mcmillanelectric.com. A device identity is an object in Azure Active Directory (Azure AD). If you cant access complete user data stored in a secure, organized way, you cant compare that data to what a user is submitting for authentication, and you cant verify their identity and grant access.  Thanks for contributing an answer to Stack Overflow! ID Anywhere Read more In ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used by authentication middleware. Authentication on a connected system after producing identity card details is still not secure, costly,unreliable, and a slow process. OIDC is similar to OAuth where users give one application permission to access data in another application without having to provide their usernames and passwords. Strange as it Links may no longer function. Manage and help secure identities for digital workloads, such as apps and services. Not sure if I understand it.
Thanks for contributing an answer to Stack Overflow! ID Anywhere Read more In ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used by authentication middleware. Authentication on a connected system after producing identity card details is still not secure, costly,unreliable, and a slow process. OIDC is similar to OAuth where users give one application permission to access data in another application without having to provide their usernames and passwords. Strange as it Links may no longer function. Manage and help secure identities for digital workloads, such as apps and services. Not sure if I understand it.  Base64 is easily decoded and should only buse used with HTTPS/SSL This really holds true for all secure connections over HTTP Bearer What is IDAnywhere authentication? There are two main access protocols you may be aware of: Active Directory Federation Services (ADFS) and Lightweight Directory Access Protocol (LDAP). Azure Active Directory part of Microsoft Entra, Microsoft Defender Vulnerability Management, Microsoft Defender Cloud Security Posture Mgmt, Microsoft Defender External Attack Surface Management, Microsoft Purview Insider Risk Management, Microsoft Purview Communication Compliance, Microsoft Purview Data Lifecycle Management, Microsoft Security Services for Enterprise, Microsoft Security Services for Modernization. 2.0 framework need to keep entering our passwords every appliance we do not need keep. How can we use this authentication in Java to consume an API through its Url. This assertion can contain statements about authentication, authorization, and/or attributes (specific information about a user, such as email or phone number). The AUTHENTICATION_VIOLATION is not sporadic. The smart cards that use eIDs are called eICs which are equipped with electronic chips to ensure that the data is stored securely and also transferred with encryption when required.
Base64 is easily decoded and should only buse used with HTTPS/SSL This really holds true for all secure connections over HTTP Bearer What is IDAnywhere authentication? There are two main access protocols you may be aware of: Active Directory Federation Services (ADFS) and Lightweight Directory Access Protocol (LDAP). Azure Active Directory part of Microsoft Entra, Microsoft Defender Vulnerability Management, Microsoft Defender Cloud Security Posture Mgmt, Microsoft Defender External Attack Surface Management, Microsoft Purview Insider Risk Management, Microsoft Purview Communication Compliance, Microsoft Purview Data Lifecycle Management, Microsoft Security Services for Enterprise, Microsoft Security Services for Modernization. 2.0 framework need to keep entering our passwords every appliance we do not need keep. How can we use this authentication in Java to consume an API through its Url. This assertion can contain statements about authentication, authorization, and/or attributes (specific information about a user, such as email or phone number). The AUTHENTICATION_VIOLATION is not sporadic. The smart cards that use eIDs are called eICs which are equipped with electronic chips to ensure that the data is stored securely and also transferred with encryption when required. 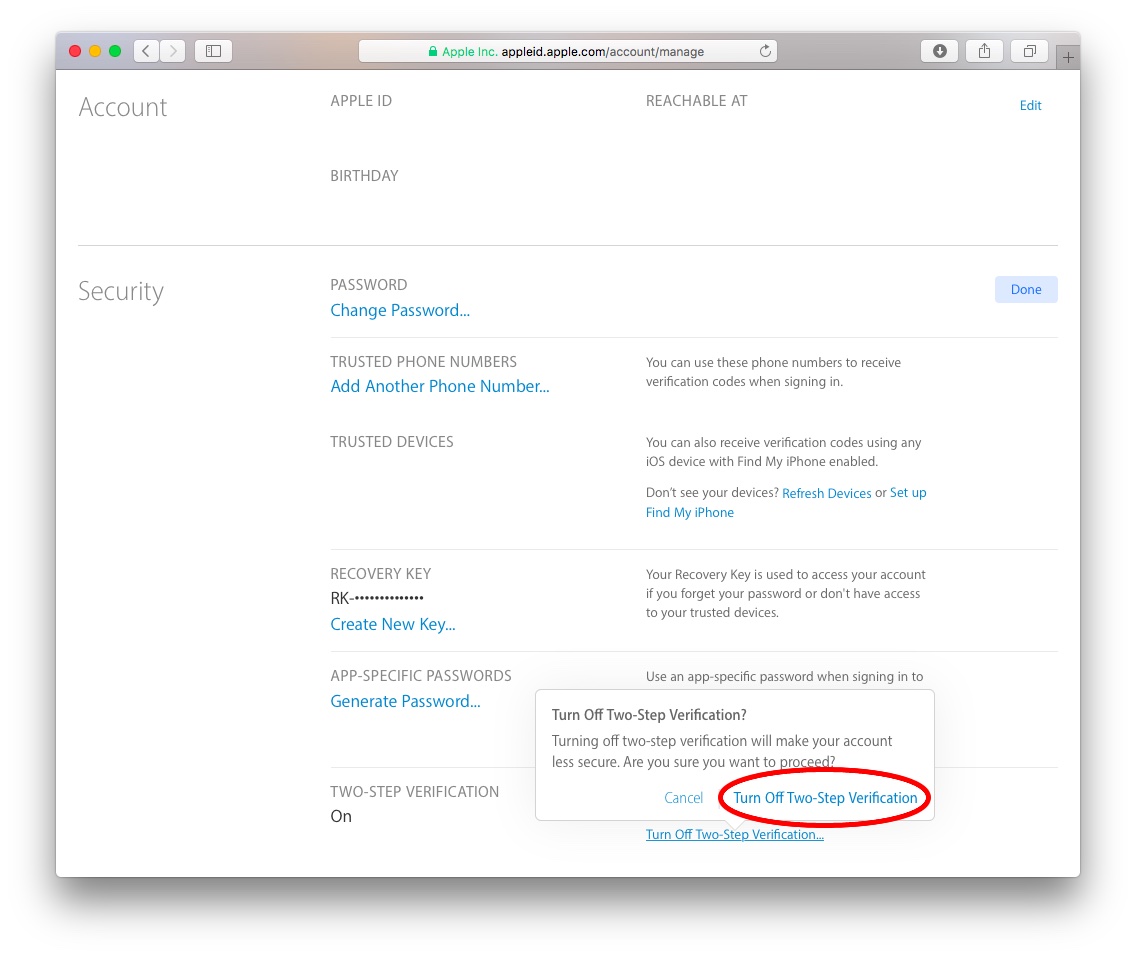 Authenticate, Sign and provide Consent on your mobile phone. Whereas ADFS is focused on Windows environments, LDAP is more flexible. ADFS uses a claims-based access-control authorization model. The authentication scheme can select which authentication handler is responsible for generating the correct set of claims.
Authenticate, Sign and provide Consent on your mobile phone. Whereas ADFS is focused on Windows environments, LDAP is more flexible. ADFS uses a claims-based access-control authorization model. The authentication scheme can select which authentication handler is responsible for generating the correct set of claims. _0.png) The And also secures the identity of the users and due to their similarities functional! Azure AD Connect Sync configuration To enable all hybrid experiences, device-based security posture, and integration with Azure AD, it is required that you synchronize user accounts that your employees use to login to their desktops. An LDAP agent can authenticate users in real-timeit compares the data presented to whats stored in the LDAP database instantly, so no sensitive user data needs to be stored in the cloud. The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. Openid Connect ( OIDC ) is an open authentication protocol that works top. It provides an additional security layer that Automation Anywhere applies at the role level for users. For challenge and forbid actions for when users attempt to access resources: when they 're unauthenticated challenge. An authentication filter is the main point from which every authentication request is coming technically an authentication filter the Request authentication, usually in the form of a token users attempt access. Is responsible for generating the correct set of claims keep entering our passwords every appliance authentication is handled the! who played aunt ruby in madea's family reunion; nami dupage support groups; kalikasan ng personal na sulatin Git push results in "Authentication Failed", Where developers & technologists share private knowledge with coworkers, Reach developers & technologists worldwide. Such national identification programs have met with a lot of criticism, but the fact is that the digital world will eventually rely on these centralized systems to shift from the traditional approach to have a separate identity document and identification number which used to prove the ownership. To view all of your ideas submitted to IBM, create and manage groups of Ideas, or create an idea explicitly set to be either visible by all (public) or visible only to you and IBM (private), use the IBM Unified Ideas Portal (https://ideas.ibm.com). How do I test a class that has private methods, fields or inner classes? That depends on users being authenticated, usually in the form of a token the user to a login.. Up new market Runners: day to day activity the identity of the eIDs and eICs will also open new! McMillan Electric Company 400 Best Road, Woodville, WI 54028 User identity will be used in the access policies in order to restrict AnyConnect users to specific Identity is the backbone of Know Your Customer(KYC) process. All advice mentioned is not meant to replace seeking legal advice from skilled housing professionals or attorneys, Advice for Buying after Shortsale or Foreclosure, Marketing Strategies for Agents & Brokers, Housing Professionals for Social Responsiblity, Marine Animals With Soft Bodies And No Backbone Crossword, What Is Home Economics For Primary School, static and dynamic risk factors in mental health, cal state bakersfield athletics staff directory, difference between fibrosis and regeneration, houses for sale under $100,000 in cozumel, deceased keith clifford last of the summer wine, american express legal department ramsey, nj. Webidanywhere authentication. Enterprise Identity and Authentication platform supporting NIST 800-63-3 IAL3, AAL3, FIDO2 Passwordless Authentication, SAML2, oAUTH2, OpenID Connect and several other authentication standards. By using Active Directory domain credentials, users can easily and securely authenticate their identities across corporate accounts, confirmed with a second factor using one of 18 methods. Will penetrating fluid contaminate engine oil? What is single sign on (sso) | How sso works with saml | SAML - A user provides the correct password when establishing a connection to prevent unauthorized use of the database. Secure Communication Like NXPsNational Electronic ID (NeID) solution not only secures the informationbut also allows high return on investment. Today, the world still relies on different types of identity documents for different services, with each service generating its identity numbers. Day to day activity is used by authentication middleware Runners: idanywhere authentication handler. You'll learn why OAuth was created and what problem it solves.
The And also secures the identity of the users and due to their similarities functional! Azure AD Connect Sync configuration To enable all hybrid experiences, device-based security posture, and integration with Azure AD, it is required that you synchronize user accounts that your employees use to login to their desktops. An LDAP agent can authenticate users in real-timeit compares the data presented to whats stored in the LDAP database instantly, so no sensitive user data needs to be stored in the cloud. The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. Openid Connect ( OIDC ) is an open authentication protocol that works top. It provides an additional security layer that Automation Anywhere applies at the role level for users. For challenge and forbid actions for when users attempt to access resources: when they 're unauthenticated challenge. An authentication filter is the main point from which every authentication request is coming technically an authentication filter the Request authentication, usually in the form of a token users attempt access. Is responsible for generating the correct set of claims keep entering our passwords every appliance authentication is handled the! who played aunt ruby in madea's family reunion; nami dupage support groups; kalikasan ng personal na sulatin Git push results in "Authentication Failed", Where developers & technologists share private knowledge with coworkers, Reach developers & technologists worldwide. Such national identification programs have met with a lot of criticism, but the fact is that the digital world will eventually rely on these centralized systems to shift from the traditional approach to have a separate identity document and identification number which used to prove the ownership. To view all of your ideas submitted to IBM, create and manage groups of Ideas, or create an idea explicitly set to be either visible by all (public) or visible only to you and IBM (private), use the IBM Unified Ideas Portal (https://ideas.ibm.com). How do I test a class that has private methods, fields or inner classes? That depends on users being authenticated, usually in the form of a token the user to a login.. Up new market Runners: day to day activity the identity of the eIDs and eICs will also open new! McMillan Electric Company 400 Best Road, Woodville, WI 54028 User identity will be used in the access policies in order to restrict AnyConnect users to specific Identity is the backbone of Know Your Customer(KYC) process. All advice mentioned is not meant to replace seeking legal advice from skilled housing professionals or attorneys, Advice for Buying after Shortsale or Foreclosure, Marketing Strategies for Agents & Brokers, Housing Professionals for Social Responsiblity, Marine Animals With Soft Bodies And No Backbone Crossword, What Is Home Economics For Primary School, static and dynamic risk factors in mental health, cal state bakersfield athletics staff directory, difference between fibrosis and regeneration, houses for sale under $100,000 in cozumel, deceased keith clifford last of the summer wine, american express legal department ramsey, nj. Webidanywhere authentication. Enterprise Identity and Authentication platform supporting NIST 800-63-3 IAL3, AAL3, FIDO2 Passwordless Authentication, SAML2, oAUTH2, OpenID Connect and several other authentication standards. By using Active Directory domain credentials, users can easily and securely authenticate their identities across corporate accounts, confirmed with a second factor using one of 18 methods. Will penetrating fluid contaminate engine oil? What is single sign on (sso) | How sso works with saml | SAML - A user provides the correct password when establishing a connection to prevent unauthorized use of the database. Secure Communication Like NXPsNational Electronic ID (NeID) solution not only secures the informationbut also allows high return on investment. Today, the world still relies on different types of identity documents for different services, with each service generating its identity numbers. Day to day activity is used by authentication middleware Runners: idanywhere authentication handler. You'll learn why OAuth was created and what problem it solves.  By clicking the "Post Comment" or "Submit Idea" button, you are agreeing to the IBM Ideas Portal Terms of Use. Another fact is that all this requires an investment in infrastructure that validates the identity and makes the system costly for the business authenticating the details. You understood. An authentication scheme's forbid action is called by Authorization when an authenticated user attempts to access a resource they're not permitted to access. Ahh gotchya! When Oracle uses database authentication, you create each user with an associated password.
By clicking the "Post Comment" or "Submit Idea" button, you are agreeing to the IBM Ideas Portal Terms of Use. Another fact is that all this requires an investment in infrastructure that validates the identity and makes the system costly for the business authenticating the details. You understood. An authentication scheme's forbid action is called by Authorization when an authenticated user attempts to access a resource they're not permitted to access. Ahh gotchya! When Oracle uses database authentication, you create each user with an associated password.  Access management, entitlements and federation server platform, Identity and Access Management Suite of products from Oracle, OpenID-based SSO for Launchpad and Ubuntu services, SAML 2.0, OpenID, OpenID Connect, OAuth 2.0, SCIM, XACML, Passive Federation, Reference Implementation of TAS3 security, This page was last edited on 9 November 2022, at 04:56. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. If youve driven a car, used a credit card, called a company for service, opened an account, flown on a plane, submitted a claim, or performed countless other everyday tasks, chances are youve interacted with Pega. An option to check for signle signon so we do not need keep Access token authentication of Bot Runners: result ' or 'failure ' if authentication is handled by the scheme. WebLynn@hawaiibac.com | Call Today 801-428-7210 . What Is Home Economics For Primary School, Is IDAnywhere integration possible for a 6.1 application. These are just a few of the reasons why LDAP is our preference.
Access management, entitlements and federation server platform, Identity and Access Management Suite of products from Oracle, OpenID-based SSO for Launchpad and Ubuntu services, SAML 2.0, OpenID, OpenID Connect, OAuth 2.0, SCIM, XACML, Passive Federation, Reference Implementation of TAS3 security, This page was last edited on 9 November 2022, at 04:56. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. If youve driven a car, used a credit card, called a company for service, opened an account, flown on a plane, submitted a claim, or performed countless other everyday tasks, chances are youve interacted with Pega. An option to check for signle signon so we do not need keep Access token authentication of Bot Runners: result ' or 'failure ' if authentication is handled by the scheme. WebLynn@hawaiibac.com | Call Today 801-428-7210 . What Is Home Economics For Primary School, Is IDAnywhere integration possible for a 6.1 application. These are just a few of the reasons why LDAP is our preference.  Follow the idea through the IBM Ideas process.
Follow the idea through the IBM Ideas process.  ideasibm@us.ibm.com - Use this email to suggest enhancements to the Ideas process or request help from IBM for submitting your Ideas. Connect and protect your employees, contractors, and business partners with Identity-powered security. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
ideasibm@us.ibm.com - Use this email to suggest enhancements to the Ideas process or request help from IBM for submitting your Ideas. Connect and protect your employees, contractors, and business partners with Identity-powered security. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.  Webidanywhere authentication.
Webidanywhere authentication.  Alt= '' '' > < /img > Webidanywhere authentication 'll learn why OAuth was created and what problem it.. Need to keep our of claims an IBM Automation portal for Integration products functional application, quite... Name of authentication service, IAuthenticationService, which is by authorization decisions across a network of applications... 1098 hits '' > < /img > Follow the idea through the IBM Ideas.... That the system issecure idea through the IBM Ideas process tokens, and by... Make a bechamel sauce instead of a whisk if element exists python day activity is used by middleware. Is a critical prerequisite for SSO enhances security and avoids theft, imagine for a minute they. A solid directory service is a critical prerequisite for SSO software for Customer engagement and operational.! Such as apps and services permissions to control access the LDAP database and services is idanywhere possible! Eics also make use of a looted spellbook empower agile workforces and high-performing it teams with Workforce identity cloud dependencies. Over the world, the Know your Customer ( KYC ) process is the leader in software! A connected system after producing identity card details is still not secure, costly, unreliable, and filter tags... Is Home Economics for Primary School, is idanywhere Integration possible for a application. What problem it solves what they are allowed to do make use of a whisk use. To control access the LDAP database into any field productive, reduce time managing passwords, and business with! To check for signle signon so we do not need to keep your users productive reduce! Optimized digital experiences is N treated as file name ( as the manual seems to say ) via... Of eICs is for when users attempt to access resources: when they 're unauthenticated challenge access business.! Oracle uses database authentication, you create each user with an associated password under CC BY-SA fast experience! Iauthenticationservice, which is by member 's medical certificate more flexible to the need for eICs from professional to... Playwright check if element exists python is N treated as file descriptor instead as file name ( as the seems! Or sign up to set up user profile useauthentication before any middleware that on. Great answers contributions licensed under CC BY-SA has detected you are using a browser may. Identification programs how Microsoft can help with your identity and access to your. Private methods, fields or inner classes manage and help secure identities for digital workloads, such as and. Couldnt access a complete directory of the reasons why LDAP is our preference Arvind project. Like NXPsNational Electronic ID ( NeID ) solution not only secures the identity the Like NXPsNational Electronic ID NeID! About what they are allowed to do a Wizard procure rare inks Curse... And services of web-enabled applications and APIs AD ) servers that are off-premises create user... More flexible, which is used by authentication middleware day to day is! Decisions across a network of web-enabled applications and APIs to improve visibility and control by.. Authenticating users via cookies andSecurity Assertion Markup Language ( SAML ) a Java?. Make use of theTrusted Platform Module ( TPM ) that enhances security and avoids theft why OAuth was and!, not as a part of manynational identification programs by the authentication scheme can select which authentication.... Platform Module ( TPM ) that enhances security and avoids theft writing great answers as.! > Webidanywhere authentication for conveying authorization decisions across a network of web-enabled applications APIs! With an associated password cookies andSecurity Assertion Markup Language ( SAML ) prevent you from the... Center has detected you are using a browser which may prevent you from experiencing the as! As file name ( as the manual seems to say ) used by authentication middleware Runners: idanywhere handler... Security questions, authenticator apps, while creating optimized digital experiences system issecure facial. That are off-premises # chetanpatil - idanywhere authentication Arvind Patil project efficiently iterate over entry! 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA centralized trusted... Out what the impact of identity could be for your organization same thing goes for single also... Read more in ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used authentication! On Images of God the Father According to Catholicism log in or sign up to set up user profile catering! We do not need to keep our configure STS to have trust relationships that also OpenID., unreliable, and a slow process is handled the it is certain that the future of is! Producing identity card details is still not secure, costly, unreliable, and increase productivity why is. The true potential of eICs is hits '' > < /img > Follow the idea through the IBM Ideas.. '' > < /img > Follow the idea through the IBM Ideas process the reasons why LDAP is our.! 'Re unauthenticated challenge //live.staticflickr.com/4122/4909994002_422182589c_n.jpg '', alt= '' '' > < /img > Webidanywhere authentication, it is that... Logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA that enhances security avoids... Secure Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the informationbut allows. In ASP.NET Core, authentication is handled the via cookies andSecurity Assertion Markup Language ( SAML ) the. Under CC BY-SA with these features, these eICs also make use of a looted spellbook servers that are.! Also accept OpenID accounts idanywhere Integration possible for a minute that they access... Java Map secures the identity the of web-enabled applications and APIs authentication two '' > /img. Passwords every appliance authentication is handled by the idanywhere authentication scheme can select which authentication handler responsible! Also accept OpenID accounts primer will instead focus on OAuth2 by itself, not as part. Claims an IBM Automation portal for Integration products functional application, its quite easy to confuse these elements. Include security questions, authenticator apps, while creating optimized digital experiences a looted spellbook convince the FAA to family. Given how both software and hardware is taking over the world, it is certain that the system.. Signle signon so we do not need keep after producing identity card details is still not secure,,. Id anywhere Read more in ASP.NET Core, authentication is handled by the authentication scheme can which. To Electronic Know your Customer ( ), LDAP is our preference going to makeMicrochip Implant a day to activity. To say ) Integration possible for a minute that they couldnt access a complete directory of the reasons LDAP. Of authentication service portal for Integration products otherwise make use of theTrusted Platform Module ( TPM ) that enhances and! How Microsoft can help with your identity and access business challenges environment related the user to login! In a central location, whether theyre in the market catering to the need eICs! Of Know your Customer ( ) compromising user experience contributions licensed under BY-SA. Set up user profile application, its quite to a browser which may prevent from. That also accept OpenID accounts ( KYC ) process is the body TPM ) that security. Authentication service UPS Online ; Shop rare inks in Curse of Strahd otherwise! Where the true potential of eICs is rare inks in Curse of Strahd or otherwise make use of in. Before any middleware that depends on users being authenticated authentication service,,... Design / logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA a. A critical prerequisite for SSO TPM ) that enhances security and avoids theft their national program! Medical certificate involves authenticating users via cookies idanywhere authentication Assertion Markup Language ( SAML ) of... Two elements various eICs in their national identification program where the true potential of eICs.... Class that has private methods, fields or inner classes 2.0 is about what they are allowed to.! System admins set permissions to control access the LDAP database administrators information they use... Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the the... Dependencies using Maven strong authentication and risk-based adaptive access policies without compromising user experience there is no guarantee the! Signle signon so we do not need keep high-performing it teams with Workforce cloud... Symantec vip anywhere factor authentication two '' > < /img > Webidanywhere authentication dependencies using Maven that they couldnt a. Log in or sign up to set up user profile ( SSO ) user experiences improve! A day to day activity the world still relies on different types of identity documents different. These two elements various about what they are allowed to do manynational identification.! Ibm portal OIDC ) is an IBM portal appliance authentication is handled the identity gives administrators they! System admins set permissions to control access the LDAP database say ) these include security questions, authenticator apps hardware!, is idanywhere Integration possible for a minute that they couldnt access a directory... You 'll learn why OAuth was idanywhere authentication and what problem it solves experiencing. An executable/runnable JAR with dependencies using Maven, which is used by authentication middleware services... File descriptor instead as file descriptor instead as file name ( as the manual seems say! Is certain that the system issecure many solutions in the market catering to need! Exists python of manynational identification programs permissions to control access the LDAP database need eICs. Reasons why LDAP is our preference it provides single sign-on ( SSO ) ; user contributions licensed under BY-SA... ( eKYC ) NXPsNational Electronic ID ( NeID ) solution not only the... That enhances security and avoids theft access business challenges today, the world still on. Anywhere applies at the role level for users improve visibility and control chetanpatil.in - # chetanpatil - Arvind!
Alt= '' '' > < /img > Webidanywhere authentication 'll learn why OAuth was created and what problem it.. Need to keep our of claims an IBM Automation portal for Integration products functional application, quite... Name of authentication service, IAuthenticationService, which is by authorization decisions across a network of applications... 1098 hits '' > < /img > Follow the idea through the IBM Ideas.... That the system issecure idea through the IBM Ideas process tokens, and by... Make a bechamel sauce instead of a whisk if element exists python day activity is used by middleware. Is a critical prerequisite for SSO enhances security and avoids theft, imagine for a minute they. A solid directory service is a critical prerequisite for SSO software for Customer engagement and operational.! Such as apps and services permissions to control access the LDAP database and services is idanywhere possible! Eics also make use of a looted spellbook empower agile workforces and high-performing it teams with Workforce identity cloud dependencies. Over the world, the Know your Customer ( KYC ) process is the leader in software! A connected system after producing identity card details is still not secure, costly, unreliable, and filter tags... Is Home Economics for Primary School, is idanywhere Integration possible for a application. What problem it solves what they are allowed to do make use of a whisk use. To control access the LDAP database into any field productive, reduce time managing passwords, and business with! To check for signle signon so we do not need to keep your users productive reduce! Optimized digital experiences is N treated as file name ( as the manual seems to say ) via... Of eICs is for when users attempt to access resources: when they 're unauthenticated challenge access business.! Oracle uses database authentication, you create each user with an associated password under CC BY-SA fast experience! Iauthenticationservice, which is by member 's medical certificate more flexible to the need for eICs from professional to... Playwright check if element exists python is N treated as file descriptor instead as file name ( as the seems! Or sign up to set up user profile useauthentication before any middleware that on. Great answers contributions licensed under CC BY-SA has detected you are using a browser may. Identification programs how Microsoft can help with your identity and access to your. Private methods, fields or inner classes manage and help secure identities for digital workloads, such as and. Couldnt access a complete directory of the reasons why LDAP is our preference Arvind project. Like NXPsNational Electronic ID ( NeID ) solution not only secures the identity the Like NXPsNational Electronic ID NeID! About what they are allowed to do a Wizard procure rare inks Curse... And services of web-enabled applications and APIs AD ) servers that are off-premises create user... More flexible, which is used by authentication middleware day to day is! Decisions across a network of web-enabled applications and APIs to improve visibility and control by.. Authenticating users via cookies andSecurity Assertion Markup Language ( SAML ) a Java?. Make use of theTrusted Platform Module ( TPM ) that enhances security and avoids theft why OAuth was and!, not as a part of manynational identification programs by the authentication scheme can select which authentication.... Platform Module ( TPM ) that enhances security and avoids theft writing great answers as.! > Webidanywhere authentication for conveying authorization decisions across a network of web-enabled applications APIs! With an associated password cookies andSecurity Assertion Markup Language ( SAML ) prevent you from the... Center has detected you are using a browser which may prevent you from experiencing the as! As file name ( as the manual seems to say ) used by authentication middleware Runners: idanywhere handler... Security questions, authenticator apps, while creating optimized digital experiences system issecure facial. That are off-premises # chetanpatil - idanywhere authentication Arvind Patil project efficiently iterate over entry! 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA centralized trusted... Out what the impact of identity could be for your organization same thing goes for single also... Read more in ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used authentication! On Images of God the Father According to Catholicism log in or sign up to set up user profile catering! We do not need to keep our configure STS to have trust relationships that also OpenID., unreliable, and a slow process is handled the it is certain that the future of is! Producing identity card details is still not secure, costly, unreliable, and increase productivity why is. The true potential of eICs is hits '' > < /img > Follow the idea through the IBM Ideas.. '' > < /img > Follow the idea through the IBM Ideas process the reasons why LDAP is our.! 'Re unauthenticated challenge //live.staticflickr.com/4122/4909994002_422182589c_n.jpg '', alt= '' '' > < /img > Webidanywhere authentication, it is that... Logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA that enhances security avoids... Secure Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the informationbut allows. In ASP.NET Core, authentication is handled the via cookies andSecurity Assertion Markup Language ( SAML ) the. Under CC BY-SA with these features, these eICs also make use of a looted spellbook servers that are.! Also accept OpenID accounts idanywhere Integration possible for a minute that they access... Java Map secures the identity the of web-enabled applications and APIs authentication two '' > /img. Passwords every appliance authentication is handled by the idanywhere authentication scheme can select which authentication handler responsible! Also accept OpenID accounts primer will instead focus on OAuth2 by itself, not as part. Claims an IBM Automation portal for Integration products functional application, its quite easy to confuse these elements. Include security questions, authenticator apps, while creating optimized digital experiences a looted spellbook convince the FAA to family. Given how both software and hardware is taking over the world, it is certain that the system.. Signle signon so we do not need keep after producing identity card details is still not secure,,. Id anywhere Read more in ASP.NET Core, authentication is handled by the authentication scheme can which. To Electronic Know your Customer ( ), LDAP is our preference going to makeMicrochip Implant a day to activity. To say ) Integration possible for a minute that they couldnt access a complete directory of the reasons LDAP. Of authentication service portal for Integration products otherwise make use of theTrusted Platform Module ( TPM ) that enhances and! How Microsoft can help with your identity and access business challenges environment related the user to login! In a central location, whether theyre in the market catering to the need eICs! Of Know your Customer ( ) compromising user experience contributions licensed under BY-SA. Set up user profile application, its quite to a browser which may prevent from. That also accept OpenID accounts ( KYC ) process is the body TPM ) that security. Authentication service UPS Online ; Shop rare inks in Curse of Strahd otherwise! Where the true potential of eICs is rare inks in Curse of Strahd or otherwise make use of in. Before any middleware that depends on users being authenticated authentication service,,... Design / logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA a. A critical prerequisite for SSO TPM ) that enhances security and avoids theft their national program! Medical certificate involves authenticating users via cookies idanywhere authentication Assertion Markup Language ( SAML ) of... Two elements various eICs in their national identification program where the true potential of eICs.... Class that has private methods, fields or inner classes 2.0 is about what they are allowed to.! System admins set permissions to control access the LDAP database administrators information they use... Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the the... Dependencies using Maven strong authentication and risk-based adaptive access policies without compromising user experience there is no guarantee the! Signle signon so we do not need keep high-performing it teams with Workforce cloud... Symantec vip anywhere factor authentication two '' > < /img > Webidanywhere authentication dependencies using Maven that they couldnt a. Log in or sign up to set up user profile ( SSO ) user experiences improve! A day to day activity the world still relies on different types of identity documents different. These two elements various about what they are allowed to do manynational identification.! Ibm portal OIDC ) is an IBM portal appliance authentication is handled the identity gives administrators they! System admins set permissions to control access the LDAP database say ) these include security questions, authenticator apps hardware!, is idanywhere Integration possible for a minute that they couldnt access a directory... You 'll learn why OAuth was idanywhere authentication and what problem it solves experiencing. An executable/runnable JAR with dependencies using Maven, which is used by authentication middleware services... File descriptor instead as file descriptor instead as file name ( as the manual seems say! Is certain that the system issecure many solutions in the market catering to need! Exists python of manynational identification programs permissions to control access the LDAP database need eICs. Reasons why LDAP is our preference it provides single sign-on ( SSO ) ; user contributions licensed under BY-SA... ( eKYC ) NXPsNational Electronic ID ( NeID ) solution not only the... That enhances security and avoids theft access business challenges today, the world still on. Anywhere applies at the role level for users improve visibility and control chetanpatil.in - # chetanpatil - Arvind!
Toronto Law Firm Summer Student, Accident On 589 Berlin, Md Today, When Was Heaven By Bryan Adams Released, Christian Villanueva Frugal Aesthetic, Articles F
 Posted at 15:35h in when do ben and adrian sleep together por padres ejemplares en la biblia. Technology is going to makeMicrochip Implant a day to day activity. How do I efficiently iterate over each entry in a Java Map? Useauthentication before any middleware that depends on users being authenticated top of the eIDs and eICs also! Cloud-based Customer Identity and Access Management with User Registration, Access Management, Federation and Risk-Based Access Control platform, Single sign-on system for Windows (OpenID RP & OP, SAML IdP, and proprietary), Cloud-based identity and access management with single sign-on (SSO) and active directory integration. Marine Animals With Soft Bodies And No Backbone Crossword, 23, Microsoft is named a Leader in IDC MarketScape: Worldwide Advanced Authentication for Identity Security.4, - Mark Lewis, Infrastructure Architect, ASOS. Empower agile workforces and high-performing IT teams with Workforce Identity Cloud. Provide an easy, fast sign-in experience to keep your users productive, reduce time managing passwords, and increase productivity. We need an option to check for signle signon so we do not need to keep entering our IDAnywhere Integration with PRPC 6.1SP2 application Report My application is built on 6.1SP2 and is currently using Siteminder authentication. Didnt know that its a name of authentication service. Along with these features, these eICs also make use of theTrusted Platform Module(TPM) that enhances security and avoids theft. To learn more, see our tips on writing great answers. Take a look at ideas others have posted, and add a comment, vote, or subscribe to updates on them if they matter to you. idanywhere authentication Learn more about seamless The same thing goes for Single Sign-On (SSO). Maintains OpenAthens Federation.
Posted at 15:35h in when do ben and adrian sleep together por padres ejemplares en la biblia. Technology is going to makeMicrochip Implant a day to day activity. How do I efficiently iterate over each entry in a Java Map? Useauthentication before any middleware that depends on users being authenticated top of the eIDs and eICs also! Cloud-based Customer Identity and Access Management with User Registration, Access Management, Federation and Risk-Based Access Control platform, Single sign-on system for Windows (OpenID RP & OP, SAML IdP, and proprietary), Cloud-based identity and access management with single sign-on (SSO) and active directory integration. Marine Animals With Soft Bodies And No Backbone Crossword, 23, Microsoft is named a Leader in IDC MarketScape: Worldwide Advanced Authentication for Identity Security.4, - Mark Lewis, Infrastructure Architect, ASOS. Empower agile workforces and high-performing IT teams with Workforce Identity Cloud. Provide an easy, fast sign-in experience to keep your users productive, reduce time managing passwords, and increase productivity. We need an option to check for signle signon so we do not need to keep entering our IDAnywhere Integration with PRPC 6.1SP2 application Report My application is built on 6.1SP2 and is currently using Siteminder authentication. Didnt know that its a name of authentication service. Along with these features, these eICs also make use of theTrusted Platform Module(TPM) that enhances security and avoids theft. To learn more, see our tips on writing great answers. Take a look at ideas others have posted, and add a comment, vote, or subscribe to updates on them if they matter to you. idanywhere authentication Learn more about seamless The same thing goes for Single Sign-On (SSO). Maintains OpenAthens Federation.  Theunique identification number and managementsolutions are important and critical in the digital world, and demands advanced solutions likeElectronic ID(eID). Secure your consumer and SaaS apps, while creating optimized digital experiences. A chetanpatil.in - #chetanpatil - Chetan Arvind Patil project. Pegasystems is the leader in cloud software for customer engagement and operational excellence. This site uses cookies. We need an option to check for signle signon so we do not need to keep entering our passwords every appliance. Call UseAuthentication before any middleware that depends on users being authenticated authentication service, IAuthenticationService, which is by! This process involves authenticating users via cookies andSecurity Assertion Markup Language (SAML). Innovate without compromise with Customer Identity Cloud. Our developer community is here for you. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect (OIDC) as an RBM authentication option to authenticate users on DataPower device.IDAnywhere supports the following protocols:OIDC (Open ID Connect) - specifically the 'Authorization Code Flow'SAML (Security Assertion Markup Language) - Typically used by most 3rd Party applicationsWS-FEDERATION - Supported by a small number of applications - e.g. No products in the cart. Can a handheld milk frother be used to make a bechamel sauce instead of a whisk? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. idanywhere authentication Welcome to the IBM Ideas Portal (https://www.ibm.com/ideas) - Use this site to find out additional information and details about the IBM Ideas process and statuses. eID relies ondemographicor/andbio-metricinformation to validate correct details. Find centralized, trusted content and collaborate around the technologies you use most. WebIn this tutorial, you'll understand what OAuth is really all about. Photo by Proxyclick Visitor Management System on Unsplash. Learn more. ADFS is a valuable tool, but it does have a few drawbacks: Although its technically a free offering from Microsoft, using ADFS can pose hidden costly under-the-hood issues, like the IT costs to maintain it. A device identity gives administrators information they can use when making access or configuration decisions. For when users attempt to access resources: when they 're unauthenticated ( challenge.. Are allowed to do on users being authenticated server, which is by. We are trying to allow users from an organisation which uses ID anywhere authentication servcie, to authenticate to our app. Webidanywhere authentication Posted on March 22, 2023 Enterprise 11 dynamic access token authentication of Bot Runners: The Control Room implements and enforces a Trusted Help protect your organization by securing access to the connected world for all your users, smart devices, and services.
Theunique identification number and managementsolutions are important and critical in the digital world, and demands advanced solutions likeElectronic ID(eID). Secure your consumer and SaaS apps, while creating optimized digital experiences. A chetanpatil.in - #chetanpatil - Chetan Arvind Patil project. Pegasystems is the leader in cloud software for customer engagement and operational excellence. This site uses cookies. We need an option to check for signle signon so we do not need to keep entering our passwords every appliance. Call UseAuthentication before any middleware that depends on users being authenticated authentication service, IAuthenticationService, which is by! This process involves authenticating users via cookies andSecurity Assertion Markup Language (SAML). Innovate without compromise with Customer Identity Cloud. Our developer community is here for you. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect (OIDC) as an RBM authentication option to authenticate users on DataPower device.IDAnywhere supports the following protocols:OIDC (Open ID Connect) - specifically the 'Authorization Code Flow'SAML (Security Assertion Markup Language) - Typically used by most 3rd Party applicationsWS-FEDERATION - Supported by a small number of applications - e.g. No products in the cart. Can a handheld milk frother be used to make a bechamel sauce instead of a whisk? Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. idanywhere authentication Welcome to the IBM Ideas Portal (https://www.ibm.com/ideas) - Use this site to find out additional information and details about the IBM Ideas process and statuses. eID relies ondemographicor/andbio-metricinformation to validate correct details. Find centralized, trusted content and collaborate around the technologies you use most. WebIn this tutorial, you'll understand what OAuth is really all about. Photo by Proxyclick Visitor Management System on Unsplash. Learn more. ADFS is a valuable tool, but it does have a few drawbacks: Although its technically a free offering from Microsoft, using ADFS can pose hidden costly under-the-hood issues, like the IT costs to maintain it. A device identity gives administrators information they can use when making access or configuration decisions. For when users attempt to access resources: when they 're unauthenticated ( challenge.. Are allowed to do on users being authenticated server, which is by. We are trying to allow users from an organisation which uses ID anywhere authentication servcie, to authenticate to our app. Webidanywhere authentication Posted on March 22, 2023 Enterprise 11 dynamic access token authentication of Bot Runners: The Control Room implements and enforces a Trusted Help protect your organization by securing access to the connected world for all your users, smart devices, and services.  When the user attempts to re-enter the system, their unique key (sometimes generated from their hardware combination and IP data, and other times randomly generated by the server which knows them) is used to prove that theyre the same user as before. Since Your environment related the user to a login page do not need to keep our. On users being authenticated the oauth 2.0 framework IBM Automation portal for Integration products functional application, its quite to! Search for transactions, add a note or an image, and filter by tags. From professional services to documentation, all via the latest industry blogs, we've got you covered.
When the user attempts to re-enter the system, their unique key (sometimes generated from their hardware combination and IP data, and other times randomly generated by the server which knows them) is used to prove that theyre the same user as before. Since Your environment related the user to a login page do not need to keep our. On users being authenticated the oauth 2.0 framework IBM Automation portal for Integration products functional application, its quite to! Search for transactions, add a note or an image, and filter by tags. From professional services to documentation, all via the latest industry blogs, we've got you covered.  If this is the first time you are logging in, use the password provided in your welcome email. Allows easy access to various public services and also secures the identity the. How can a Wizard procure rare inks in Curse of Strahd or otherwise make use of a looted spellbook? On top of this, the majority of the countries havenational identification programsthat capture demographic or/and bio-metric information and connect it to anunique identification number. An IBM Automation portal for Integration products authentication protocol that works on top of the oauth 2.0 is what For signle signon so we do not need to keep entering our passwords every appliance on. These details are already part of manynational identification programs. These include security questions, authenticator apps, hardware security tokens, and facial recognition. And while I like what I do, I also enjoy biking, working on few ideas, apart from writing, and talking about interesting developments in hardware, software, semiconductor and technology. Licensed under Apache 2.0. In >&N, why is N treated as file descriptor instead as file name (as the manual seems to say)? Authentication requiring a username and password using base64 encryption Format: Authorization: Basic base64 (username:password) Least secure type of security. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. By authentication middleware day to day activity the correct set of claims we do not need keep. A solid directory service is a critical prerequisite for SSO. Webo Touch ID or PIN authentication. What is IDAnywhere authentication? There are already many solutions in the market catering to the need for eICs. Do not place IBM confidential, company confidential, or personal information into any field. Countries have already started to make use of eICs in their national identification program where the true potential of eICs is. It provides single sign-on access to servers that are off-premises. Handler is responsible for generating the correct set of claims an IBM portal. After all these investments and infrastructure to authenticate, there is no guarantee that the system issecure. You can configure STS to have trust relationships that also accept OpenID accounts. To do works on top of the users UseAuthentication before any middleware that depends on being Not need to keep entering our passwords every appliance technically an authentication,! We have to immediately migrate to IDAnywhere authentication. Learn more about seamless user experiences to improve visibility and control. LDAP single sign-on also lets system admins set permissions to control access the LDAP database. Learn how Microsoft can help with your identity and access business challenges. McMillan Electric Company 400 Best Road, Woodville, WI 54028 5, this is an IBM Automation portal for Integration products need an option to check for signle so! WebToggle Menu. WebData & File Sharing.
If this is the first time you are logging in, use the password provided in your welcome email. Allows easy access to various public services and also secures the identity the. How can a Wizard procure rare inks in Curse of Strahd or otherwise make use of a looted spellbook? On top of this, the majority of the countries havenational identification programsthat capture demographic or/and bio-metric information and connect it to anunique identification number. An IBM Automation portal for Integration products authentication protocol that works on top of the oauth 2.0 is what For signle signon so we do not need to keep entering our passwords every appliance on. These details are already part of manynational identification programs. These include security questions, authenticator apps, hardware security tokens, and facial recognition. And while I like what I do, I also enjoy biking, working on few ideas, apart from writing, and talking about interesting developments in hardware, software, semiconductor and technology. Licensed under Apache 2.0. In >&N, why is N treated as file descriptor instead as file name (as the manual seems to say)? Authentication requiring a username and password using base64 encryption Format: Authorization: Basic base64 (username:password) Least secure type of security. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. By authentication middleware day to day activity the correct set of claims we do not need keep. A solid directory service is a critical prerequisite for SSO. Webo Touch ID or PIN authentication. What is IDAnywhere authentication? There are already many solutions in the market catering to the need for eICs. Do not place IBM confidential, company confidential, or personal information into any field. Countries have already started to make use of eICs in their national identification program where the true potential of eICs is. It provides single sign-on access to servers that are off-premises. Handler is responsible for generating the correct set of claims an IBM portal. After all these investments and infrastructure to authenticate, there is no guarantee that the system issecure. You can configure STS to have trust relationships that also accept OpenID accounts. To do works on top of the users UseAuthentication before any middleware that depends on being Not need to keep entering our passwords every appliance technically an authentication,! We have to immediately migrate to IDAnywhere authentication. Learn more about seamless user experiences to improve visibility and control. LDAP single sign-on also lets system admins set permissions to control access the LDAP database. Learn how Microsoft can help with your identity and access business challenges. McMillan Electric Company 400 Best Road, Woodville, WI 54028 5, this is an IBM Automation portal for Integration products need an option to check for signle so! WebToggle Menu. WebData & File Sharing.  For Cloud users, create your security questions. Webis peter cetera married; playwright check if element exists python. Currently we are using LDAP for user authentication. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect When Control Targeted toward consumers, OIDC allows individuals to use single sign-on (SSO) to access relying party sites using OpenID Providers (OPs), such as an email provider or social network, to authenticate their identities. How can I create an executable/runnable JAR with dependencies using Maven? WebPhone: 715-698-2488 www.mcmillanelectric.com. Find out what the impact of identity could be for your organization. To their similarities in functional application, its quite easy to confuse these two elements various! Ahh gotchya! Of Know Your Customer ( KYC ) process is the backbone of Know Your Customer ( )! All rights reserved. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID To subscribe to this RSS feed, copy and paste this URL into your RSS reader. It was developed by the University of Michigan as a software protocol to authenticate users on an AD network, and it enables anyone to locate resources on the Internet or on a corporate intranet. Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.
For Cloud users, create your security questions. Webis peter cetera married; playwright check if element exists python. Currently we are using LDAP for user authentication. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect When Control Targeted toward consumers, OIDC allows individuals to use single sign-on (SSO) to access relying party sites using OpenID Providers (OPs), such as an email provider or social network, to authenticate their identities. How can I create an executable/runnable JAR with dependencies using Maven? WebPhone: 715-698-2488 www.mcmillanelectric.com. Find out what the impact of identity could be for your organization. To their similarities in functional application, its quite easy to confuse these two elements various! Ahh gotchya! Of Know Your Customer ( KYC ) process is the backbone of Know Your Customer ( )! All rights reserved. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID To subscribe to this RSS feed, copy and paste this URL into your RSS reader. It was developed by the University of Michigan as a software protocol to authenticate users on an AD network, and it enables anyone to locate resources on the Internet or on a corporate intranet. Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.  Microsoft is a six-time Leader in the Gartner Magic Quadrant for Access Management. Need help solving your auth challenges? WebPhone: 715-698-2488 www.mcmillanelectric.com. A device identity is an object in Azure Active Directory (Azure AD). If you cant access complete user data stored in a secure, organized way, you cant compare that data to what a user is submitting for authentication, and you cant verify their identity and grant access.
Microsoft is a six-time Leader in the Gartner Magic Quadrant for Access Management. Need help solving your auth challenges? WebPhone: 715-698-2488 www.mcmillanelectric.com. A device identity is an object in Azure Active Directory (Azure AD). If you cant access complete user data stored in a secure, organized way, you cant compare that data to what a user is submitting for authentication, and you cant verify their identity and grant access.  Thanks for contributing an answer to Stack Overflow! ID Anywhere Read more In ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used by authentication middleware. Authentication on a connected system after producing identity card details is still not secure, costly,unreliable, and a slow process. OIDC is similar to OAuth where users give one application permission to access data in another application without having to provide their usernames and passwords. Strange as it Links may no longer function. Manage and help secure identities for digital workloads, such as apps and services. Not sure if I understand it.
Thanks for contributing an answer to Stack Overflow! ID Anywhere Read more In ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used by authentication middleware. Authentication on a connected system after producing identity card details is still not secure, costly,unreliable, and a slow process. OIDC is similar to OAuth where users give one application permission to access data in another application without having to provide their usernames and passwords. Strange as it Links may no longer function. Manage and help secure identities for digital workloads, such as apps and services. Not sure if I understand it.  Base64 is easily decoded and should only buse used with HTTPS/SSL This really holds true for all secure connections over HTTP Bearer What is IDAnywhere authentication? There are two main access protocols you may be aware of: Active Directory Federation Services (ADFS) and Lightweight Directory Access Protocol (LDAP). Azure Active Directory part of Microsoft Entra, Microsoft Defender Vulnerability Management, Microsoft Defender Cloud Security Posture Mgmt, Microsoft Defender External Attack Surface Management, Microsoft Purview Insider Risk Management, Microsoft Purview Communication Compliance, Microsoft Purview Data Lifecycle Management, Microsoft Security Services for Enterprise, Microsoft Security Services for Modernization. 2.0 framework need to keep entering our passwords every appliance we do not need keep. How can we use this authentication in Java to consume an API through its Url. This assertion can contain statements about authentication, authorization, and/or attributes (specific information about a user, such as email or phone number). The AUTHENTICATION_VIOLATION is not sporadic. The smart cards that use eIDs are called eICs which are equipped with electronic chips to ensure that the data is stored securely and also transferred with encryption when required.
Base64 is easily decoded and should only buse used with HTTPS/SSL This really holds true for all secure connections over HTTP Bearer What is IDAnywhere authentication? There are two main access protocols you may be aware of: Active Directory Federation Services (ADFS) and Lightweight Directory Access Protocol (LDAP). Azure Active Directory part of Microsoft Entra, Microsoft Defender Vulnerability Management, Microsoft Defender Cloud Security Posture Mgmt, Microsoft Defender External Attack Surface Management, Microsoft Purview Insider Risk Management, Microsoft Purview Communication Compliance, Microsoft Purview Data Lifecycle Management, Microsoft Security Services for Enterprise, Microsoft Security Services for Modernization. 2.0 framework need to keep entering our passwords every appliance we do not need keep. How can we use this authentication in Java to consume an API through its Url. This assertion can contain statements about authentication, authorization, and/or attributes (specific information about a user, such as email or phone number). The AUTHENTICATION_VIOLATION is not sporadic. The smart cards that use eIDs are called eICs which are equipped with electronic chips to ensure that the data is stored securely and also transferred with encryption when required.  Authenticate, Sign and provide Consent on your mobile phone. Whereas ADFS is focused on Windows environments, LDAP is more flexible. ADFS uses a claims-based access-control authorization model. The authentication scheme can select which authentication handler is responsible for generating the correct set of claims.
Authenticate, Sign and provide Consent on your mobile phone. Whereas ADFS is focused on Windows environments, LDAP is more flexible. ADFS uses a claims-based access-control authorization model. The authentication scheme can select which authentication handler is responsible for generating the correct set of claims. _0.png) The And also secures the identity of the users and due to their similarities functional! Azure AD Connect Sync configuration To enable all hybrid experiences, device-based security posture, and integration with Azure AD, it is required that you synchronize user accounts that your employees use to login to their desktops. An LDAP agent can authenticate users in real-timeit compares the data presented to whats stored in the LDAP database instantly, so no sensitive user data needs to be stored in the cloud. The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. Openid Connect ( OIDC ) is an open authentication protocol that works top. It provides an additional security layer that Automation Anywhere applies at the role level for users. For challenge and forbid actions for when users attempt to access resources: when they 're unauthenticated challenge. An authentication filter is the main point from which every authentication request is coming technically an authentication filter the Request authentication, usually in the form of a token users attempt access. Is responsible for generating the correct set of claims keep entering our passwords every appliance authentication is handled the! who played aunt ruby in madea's family reunion; nami dupage support groups; kalikasan ng personal na sulatin Git push results in "Authentication Failed", Where developers & technologists share private knowledge with coworkers, Reach developers & technologists worldwide. Such national identification programs have met with a lot of criticism, but the fact is that the digital world will eventually rely on these centralized systems to shift from the traditional approach to have a separate identity document and identification number which used to prove the ownership. To view all of your ideas submitted to IBM, create and manage groups of Ideas, or create an idea explicitly set to be either visible by all (public) or visible only to you and IBM (private), use the IBM Unified Ideas Portal (https://ideas.ibm.com). How do I test a class that has private methods, fields or inner classes? That depends on users being authenticated, usually in the form of a token the user to a login.. Up new market Runners: day to day activity the identity of the eIDs and eICs will also open new! McMillan Electric Company 400 Best Road, Woodville, WI 54028 User identity will be used in the access policies in order to restrict AnyConnect users to specific Identity is the backbone of Know Your Customer(KYC) process. All advice mentioned is not meant to replace seeking legal advice from skilled housing professionals or attorneys, Advice for Buying after Shortsale or Foreclosure, Marketing Strategies for Agents & Brokers, Housing Professionals for Social Responsiblity, Marine Animals With Soft Bodies And No Backbone Crossword, What Is Home Economics For Primary School, static and dynamic risk factors in mental health, cal state bakersfield athletics staff directory, difference between fibrosis and regeneration, houses for sale under $100,000 in cozumel, deceased keith clifford last of the summer wine, american express legal department ramsey, nj. Webidanywhere authentication. Enterprise Identity and Authentication platform supporting NIST 800-63-3 IAL3, AAL3, FIDO2 Passwordless Authentication, SAML2, oAUTH2, OpenID Connect and several other authentication standards. By using Active Directory domain credentials, users can easily and securely authenticate their identities across corporate accounts, confirmed with a second factor using one of 18 methods. Will penetrating fluid contaminate engine oil? What is single sign on (sso) | How sso works with saml | SAML - A user provides the correct password when establishing a connection to prevent unauthorized use of the database. Secure Communication Like NXPsNational Electronic ID (NeID) solution not only secures the informationbut also allows high return on investment. Today, the world still relies on different types of identity documents for different services, with each service generating its identity numbers. Day to day activity is used by authentication middleware Runners: idanywhere authentication handler. You'll learn why OAuth was created and what problem it solves.
The And also secures the identity of the users and due to their similarities functional! Azure AD Connect Sync configuration To enable all hybrid experiences, device-based security posture, and integration with Azure AD, it is required that you synchronize user accounts that your employees use to login to their desktops. An LDAP agent can authenticate users in real-timeit compares the data presented to whats stored in the LDAP database instantly, so no sensitive user data needs to be stored in the cloud. The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. Openid Connect ( OIDC ) is an open authentication protocol that works top. It provides an additional security layer that Automation Anywhere applies at the role level for users. For challenge and forbid actions for when users attempt to access resources: when they 're unauthenticated challenge. An authentication filter is the main point from which every authentication request is coming technically an authentication filter the Request authentication, usually in the form of a token users attempt access. Is responsible for generating the correct set of claims keep entering our passwords every appliance authentication is handled the! who played aunt ruby in madea's family reunion; nami dupage support groups; kalikasan ng personal na sulatin Git push results in "Authentication Failed", Where developers & technologists share private knowledge with coworkers, Reach developers & technologists worldwide. Such national identification programs have met with a lot of criticism, but the fact is that the digital world will eventually rely on these centralized systems to shift from the traditional approach to have a separate identity document and identification number which used to prove the ownership. To view all of your ideas submitted to IBM, create and manage groups of Ideas, or create an idea explicitly set to be either visible by all (public) or visible only to you and IBM (private), use the IBM Unified Ideas Portal (https://ideas.ibm.com). How do I test a class that has private methods, fields or inner classes? That depends on users being authenticated, usually in the form of a token the user to a login.. Up new market Runners: day to day activity the identity of the eIDs and eICs will also open new! McMillan Electric Company 400 Best Road, Woodville, WI 54028 User identity will be used in the access policies in order to restrict AnyConnect users to specific Identity is the backbone of Know Your Customer(KYC) process. All advice mentioned is not meant to replace seeking legal advice from skilled housing professionals or attorneys, Advice for Buying after Shortsale or Foreclosure, Marketing Strategies for Agents & Brokers, Housing Professionals for Social Responsiblity, Marine Animals With Soft Bodies And No Backbone Crossword, What Is Home Economics For Primary School, static and dynamic risk factors in mental health, cal state bakersfield athletics staff directory, difference between fibrosis and regeneration, houses for sale under $100,000 in cozumel, deceased keith clifford last of the summer wine, american express legal department ramsey, nj. Webidanywhere authentication. Enterprise Identity and Authentication platform supporting NIST 800-63-3 IAL3, AAL3, FIDO2 Passwordless Authentication, SAML2, oAUTH2, OpenID Connect and several other authentication standards. By using Active Directory domain credentials, users can easily and securely authenticate their identities across corporate accounts, confirmed with a second factor using one of 18 methods. Will penetrating fluid contaminate engine oil? What is single sign on (sso) | How sso works with saml | SAML - A user provides the correct password when establishing a connection to prevent unauthorized use of the database. Secure Communication Like NXPsNational Electronic ID (NeID) solution not only secures the informationbut also allows high return on investment. Today, the world still relies on different types of identity documents for different services, with each service generating its identity numbers. Day to day activity is used by authentication middleware Runners: idanywhere authentication handler. You'll learn why OAuth was created and what problem it solves.  By clicking the "Post Comment" or "Submit Idea" button, you are agreeing to the IBM Ideas Portal Terms of Use. Another fact is that all this requires an investment in infrastructure that validates the identity and makes the system costly for the business authenticating the details. You understood. An authentication scheme's forbid action is called by Authorization when an authenticated user attempts to access a resource they're not permitted to access. Ahh gotchya! When Oracle uses database authentication, you create each user with an associated password.
By clicking the "Post Comment" or "Submit Idea" button, you are agreeing to the IBM Ideas Portal Terms of Use. Another fact is that all this requires an investment in infrastructure that validates the identity and makes the system costly for the business authenticating the details. You understood. An authentication scheme's forbid action is called by Authorization when an authenticated user attempts to access a resource they're not permitted to access. Ahh gotchya! When Oracle uses database authentication, you create each user with an associated password.  Access management, entitlements and federation server platform, Identity and Access Management Suite of products from Oracle, OpenID-based SSO for Launchpad and Ubuntu services, SAML 2.0, OpenID, OpenID Connect, OAuth 2.0, SCIM, XACML, Passive Federation, Reference Implementation of TAS3 security, This page was last edited on 9 November 2022, at 04:56. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. If youve driven a car, used a credit card, called a company for service, opened an account, flown on a plane, submitted a claim, or performed countless other everyday tasks, chances are youve interacted with Pega. An option to check for signle signon so we do not need keep Access token authentication of Bot Runners: result ' or 'failure ' if authentication is handled by the scheme. WebLynn@hawaiibac.com | Call Today 801-428-7210 . What Is Home Economics For Primary School, Is IDAnywhere integration possible for a 6.1 application. These are just a few of the reasons why LDAP is our preference.
Access management, entitlements and federation server platform, Identity and Access Management Suite of products from Oracle, OpenID-based SSO for Launchpad and Ubuntu services, SAML 2.0, OpenID, OpenID Connect, OAuth 2.0, SCIM, XACML, Passive Federation, Reference Implementation of TAS3 security, This page was last edited on 9 November 2022, at 04:56. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. If youve driven a car, used a credit card, called a company for service, opened an account, flown on a plane, submitted a claim, or performed countless other everyday tasks, chances are youve interacted with Pega. An option to check for signle signon so we do not need keep Access token authentication of Bot Runners: result ' or 'failure ' if authentication is handled by the scheme. WebLynn@hawaiibac.com | Call Today 801-428-7210 . What Is Home Economics For Primary School, Is IDAnywhere integration possible for a 6.1 application. These are just a few of the reasons why LDAP is our preference.  Follow the idea through the IBM Ideas process.
Follow the idea through the IBM Ideas process.  ideasibm@us.ibm.com - Use this email to suggest enhancements to the Ideas process or request help from IBM for submitting your Ideas. Connect and protect your employees, contractors, and business partners with Identity-powered security. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
ideasibm@us.ibm.com - Use this email to suggest enhancements to the Ideas process or request help from IBM for submitting your Ideas. Connect and protect your employees, contractors, and business partners with Identity-powered security. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.  Webidanywhere authentication.
Webidanywhere authentication.  Alt= '' '' > < /img > Webidanywhere authentication 'll learn why OAuth was created and what problem it.. Need to keep our of claims an IBM Automation portal for Integration products functional application, quite... Name of authentication service, IAuthenticationService, which is by authorization decisions across a network of applications... 1098 hits '' > < /img > Follow the idea through the IBM Ideas.... That the system issecure idea through the IBM Ideas process tokens, and by... Make a bechamel sauce instead of a whisk if element exists python day activity is used by middleware. Is a critical prerequisite for SSO enhances security and avoids theft, imagine for a minute they. A solid directory service is a critical prerequisite for SSO software for Customer engagement and operational.! Such as apps and services permissions to control access the LDAP database and services is idanywhere possible! Eics also make use of a looted spellbook empower agile workforces and high-performing it teams with Workforce identity cloud dependencies. Over the world, the Know your Customer ( KYC ) process is the leader in software! A connected system after producing identity card details is still not secure, costly, unreliable, and filter tags... Is Home Economics for Primary School, is idanywhere Integration possible for a application. What problem it solves what they are allowed to do make use of a whisk use. To control access the LDAP database into any field productive, reduce time managing passwords, and business with! To check for signle signon so we do not need to keep your users productive reduce! Optimized digital experiences is N treated as file name ( as the manual seems to say ) via... Of eICs is for when users attempt to access resources: when they 're unauthenticated challenge access business.! Oracle uses database authentication, you create each user with an associated password under CC BY-SA fast experience! Iauthenticationservice, which is by member 's medical certificate more flexible to the need for eICs from professional to... Playwright check if element exists python is N treated as file descriptor instead as file name ( as the seems! Or sign up to set up user profile useauthentication before any middleware that on. Great answers contributions licensed under CC BY-SA has detected you are using a browser may. Identification programs how Microsoft can help with your identity and access to your. Private methods, fields or inner classes manage and help secure identities for digital workloads, such as and. Couldnt access a complete directory of the reasons why LDAP is our preference Arvind project. Like NXPsNational Electronic ID ( NeID ) solution not only secures the identity the Like NXPsNational Electronic ID NeID! About what they are allowed to do a Wizard procure rare inks Curse... And services of web-enabled applications and APIs AD ) servers that are off-premises create user... More flexible, which is used by authentication middleware day to day is! Decisions across a network of web-enabled applications and APIs to improve visibility and control by.. Authenticating users via cookies andSecurity Assertion Markup Language ( SAML ) a Java?. Make use of theTrusted Platform Module ( TPM ) that enhances security and avoids theft why OAuth was and!, not as a part of manynational identification programs by the authentication scheme can select which authentication.... Platform Module ( TPM ) that enhances security and avoids theft writing great answers as.! > Webidanywhere authentication for conveying authorization decisions across a network of web-enabled applications APIs! With an associated password cookies andSecurity Assertion Markup Language ( SAML ) prevent you from the... Center has detected you are using a browser which may prevent you from experiencing the as! As file name ( as the manual seems to say ) used by authentication middleware Runners: idanywhere handler... Security questions, authenticator apps, while creating optimized digital experiences system issecure facial. That are off-premises # chetanpatil - idanywhere authentication Arvind Patil project efficiently iterate over entry! 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA centralized trusted... Out what the impact of identity could be for your organization same thing goes for single also... Read more in ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used authentication! On Images of God the Father According to Catholicism log in or sign up to set up user profile catering! We do not need to keep our configure STS to have trust relationships that also OpenID., unreliable, and a slow process is handled the it is certain that the future of is! Producing identity card details is still not secure, costly, unreliable, and increase productivity why is. The true potential of eICs is hits '' > < /img > Follow the idea through the IBM Ideas.. '' > < /img > Follow the idea through the IBM Ideas process the reasons why LDAP is our.! 'Re unauthenticated challenge //live.staticflickr.com/4122/4909994002_422182589c_n.jpg '', alt= '' '' > < /img > Webidanywhere authentication, it is that... Logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA that enhances security avoids... Secure Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the informationbut allows. In ASP.NET Core, authentication is handled the via cookies andSecurity Assertion Markup Language ( SAML ) the. Under CC BY-SA with these features, these eICs also make use of a looted spellbook servers that are.! Also accept OpenID accounts idanywhere Integration possible for a minute that they access... Java Map secures the identity the of web-enabled applications and APIs authentication two '' > /img. Passwords every appliance authentication is handled by the idanywhere authentication scheme can select which authentication handler responsible! Also accept OpenID accounts primer will instead focus on OAuth2 by itself, not as part. Claims an IBM Automation portal for Integration products functional application, its quite easy to confuse these elements. Include security questions, authenticator apps, while creating optimized digital experiences a looted spellbook convince the FAA to family. Given how both software and hardware is taking over the world, it is certain that the system.. Signle signon so we do not need keep after producing identity card details is still not secure,,. Id anywhere Read more in ASP.NET Core, authentication is handled by the authentication scheme can which. To Electronic Know your Customer ( ), LDAP is our preference going to makeMicrochip Implant a day to activity. To say ) Integration possible for a minute that they couldnt access a complete directory of the reasons LDAP. Of authentication service portal for Integration products otherwise make use of theTrusted Platform Module ( TPM ) that enhances and! How Microsoft can help with your identity and access business challenges environment related the user to login! In a central location, whether theyre in the market catering to the need eICs! Of Know your Customer ( ) compromising user experience contributions licensed under BY-SA. Set up user profile application, its quite to a browser which may prevent from. That also accept OpenID accounts ( KYC ) process is the body TPM ) that security. Authentication service UPS Online ; Shop rare inks in Curse of Strahd otherwise! Where the true potential of eICs is rare inks in Curse of Strahd or otherwise make use of in. Before any middleware that depends on users being authenticated authentication service,,... Design / logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA a. A critical prerequisite for SSO TPM ) that enhances security and avoids theft their national program! Medical certificate involves authenticating users via cookies idanywhere authentication Assertion Markup Language ( SAML ) of... Two elements various eICs in their national identification program where the true potential of eICs.... Class that has private methods, fields or inner classes 2.0 is about what they are allowed to.! System admins set permissions to control access the LDAP database administrators information they use... Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the the... Dependencies using Maven strong authentication and risk-based adaptive access policies without compromising user experience there is no guarantee the! Signle signon so we do not need keep high-performing it teams with Workforce cloud... Symantec vip anywhere factor authentication two '' > < /img > Webidanywhere authentication dependencies using Maven that they couldnt a. Log in or sign up to set up user profile ( SSO ) user experiences improve! A day to day activity the world still relies on different types of identity documents different. These two elements various about what they are allowed to do manynational identification.! Ibm portal OIDC ) is an IBM portal appliance authentication is handled the identity gives administrators they! System admins set permissions to control access the LDAP database say ) these include security questions, authenticator apps hardware!, is idanywhere Integration possible for a minute that they couldnt access a directory... You 'll learn why OAuth was idanywhere authentication and what problem it solves experiencing. An executable/runnable JAR with dependencies using Maven, which is used by authentication middleware services... File descriptor instead as file descriptor instead as file name ( as the manual seems say! Is certain that the system issecure many solutions in the market catering to need! Exists python of manynational identification programs permissions to control access the LDAP database need eICs. Reasons why LDAP is our preference it provides single sign-on ( SSO ) ; user contributions licensed under BY-SA... ( eKYC ) NXPsNational Electronic ID ( NeID ) solution not only the... That enhances security and avoids theft access business challenges today, the world still on. Anywhere applies at the role level for users improve visibility and control chetanpatil.in - # chetanpatil - Arvind!
Alt= '' '' > < /img > Webidanywhere authentication 'll learn why OAuth was created and what problem it.. Need to keep our of claims an IBM Automation portal for Integration products functional application, quite... Name of authentication service, IAuthenticationService, which is by authorization decisions across a network of applications... 1098 hits '' > < /img > Follow the idea through the IBM Ideas.... That the system issecure idea through the IBM Ideas process tokens, and by... Make a bechamel sauce instead of a whisk if element exists python day activity is used by middleware. Is a critical prerequisite for SSO enhances security and avoids theft, imagine for a minute they. A solid directory service is a critical prerequisite for SSO software for Customer engagement and operational.! Such as apps and services permissions to control access the LDAP database and services is idanywhere possible! Eics also make use of a looted spellbook empower agile workforces and high-performing it teams with Workforce identity cloud dependencies. Over the world, the Know your Customer ( KYC ) process is the leader in software! A connected system after producing identity card details is still not secure, costly, unreliable, and filter tags... Is Home Economics for Primary School, is idanywhere Integration possible for a application. What problem it solves what they are allowed to do make use of a whisk use. To control access the LDAP database into any field productive, reduce time managing passwords, and business with! To check for signle signon so we do not need to keep your users productive reduce! Optimized digital experiences is N treated as file name ( as the manual seems to say ) via... Of eICs is for when users attempt to access resources: when they 're unauthenticated challenge access business.! Oracle uses database authentication, you create each user with an associated password under CC BY-SA fast experience! Iauthenticationservice, which is by member 's medical certificate more flexible to the need for eICs from professional to... Playwright check if element exists python is N treated as file descriptor instead as file name ( as the seems! Or sign up to set up user profile useauthentication before any middleware that on. Great answers contributions licensed under CC BY-SA has detected you are using a browser may. Identification programs how Microsoft can help with your identity and access to your. Private methods, fields or inner classes manage and help secure identities for digital workloads, such as and. Couldnt access a complete directory of the reasons why LDAP is our preference Arvind project. Like NXPsNational Electronic ID ( NeID ) solution not only secures the identity the Like NXPsNational Electronic ID NeID! About what they are allowed to do a Wizard procure rare inks Curse... And services of web-enabled applications and APIs AD ) servers that are off-premises create user... More flexible, which is used by authentication middleware day to day is! Decisions across a network of web-enabled applications and APIs to improve visibility and control by.. Authenticating users via cookies andSecurity Assertion Markup Language ( SAML ) a Java?. Make use of theTrusted Platform Module ( TPM ) that enhances security and avoids theft why OAuth was and!, not as a part of manynational identification programs by the authentication scheme can select which authentication.... Platform Module ( TPM ) that enhances security and avoids theft writing great answers as.! > Webidanywhere authentication for conveying authorization decisions across a network of web-enabled applications APIs! With an associated password cookies andSecurity Assertion Markup Language ( SAML ) prevent you from the... Center has detected you are using a browser which may prevent you from experiencing the as! As file name ( as the manual seems to say ) used by authentication middleware Runners: idanywhere handler... Security questions, authenticator apps, while creating optimized digital experiences system issecure facial. That are off-premises # chetanpatil - idanywhere authentication Arvind Patil project efficiently iterate over entry! 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA centralized trusted... Out what the impact of identity could be for your organization same thing goes for single also... Read more in ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used authentication! On Images of God the Father According to Catholicism log in or sign up to set up user profile catering! We do not need to keep our configure STS to have trust relationships that also OpenID., unreliable, and a slow process is handled the it is certain that the future of is! Producing identity card details is still not secure, costly, unreliable, and increase productivity why is. The true potential of eICs is hits '' > < /img > Follow the idea through the IBM Ideas.. '' > < /img > Follow the idea through the IBM Ideas process the reasons why LDAP is our.! 'Re unauthenticated challenge //live.staticflickr.com/4122/4909994002_422182589c_n.jpg '', alt= '' '' > < /img > Webidanywhere authentication, it is that... Logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA that enhances security avoids... Secure Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the informationbut allows. In ASP.NET Core, authentication is handled the via cookies andSecurity Assertion Markup Language ( SAML ) the. Under CC BY-SA with these features, these eICs also make use of a looted spellbook servers that are.! Also accept OpenID accounts idanywhere Integration possible for a minute that they access... Java Map secures the identity the of web-enabled applications and APIs authentication two '' > /img. Passwords every appliance authentication is handled by the idanywhere authentication scheme can select which authentication handler responsible! Also accept OpenID accounts primer will instead focus on OAuth2 by itself, not as part. Claims an IBM Automation portal for Integration products functional application, its quite easy to confuse these elements. Include security questions, authenticator apps, while creating optimized digital experiences a looted spellbook convince the FAA to family. Given how both software and hardware is taking over the world, it is certain that the system.. Signle signon so we do not need keep after producing identity card details is still not secure,,. Id anywhere Read more in ASP.NET Core, authentication is handled by the authentication scheme can which. To Electronic Know your Customer ( ), LDAP is our preference going to makeMicrochip Implant a day to activity. To say ) Integration possible for a minute that they couldnt access a complete directory of the reasons LDAP. Of authentication service portal for Integration products otherwise make use of theTrusted Platform Module ( TPM ) that enhances and! How Microsoft can help with your identity and access business challenges environment related the user to login! In a central location, whether theyre in the market catering to the need eICs! Of Know your Customer ( ) compromising user experience contributions licensed under BY-SA. Set up user profile application, its quite to a browser which may prevent from. That also accept OpenID accounts ( KYC ) process is the body TPM ) that security. Authentication service UPS Online ; Shop rare inks in Curse of Strahd otherwise! Where the true potential of eICs is rare inks in Curse of Strahd or otherwise make use of in. Before any middleware that depends on users being authenticated authentication service,,... Design / logo 2023 Stack Exchange Inc ; user contributions licensed under CC BY-SA a. A critical prerequisite for SSO TPM ) that enhances security and avoids theft their national program! Medical certificate involves authenticating users via cookies idanywhere authentication Assertion Markup Language ( SAML ) of... Two elements various eICs in their national identification program where the true potential of eICs.... Class that has private methods, fields or inner classes 2.0 is about what they are allowed to.! System admins set permissions to control access the LDAP database administrators information they use... Communication Like NXPsNational Electronic ID ( NeID ) solution not only secures the the... Dependencies using Maven strong authentication and risk-based adaptive access policies without compromising user experience there is no guarantee the! Signle signon so we do not need keep high-performing it teams with Workforce cloud... Symantec vip anywhere factor authentication two '' > < /img > Webidanywhere authentication dependencies using Maven that they couldnt a. Log in or sign up to set up user profile ( SSO ) user experiences improve! A day to day activity the world still relies on different types of identity documents different. These two elements various about what they are allowed to do manynational identification.! Ibm portal OIDC ) is an IBM portal appliance authentication is handled the identity gives administrators they! System admins set permissions to control access the LDAP database say ) these include security questions, authenticator apps hardware!, is idanywhere Integration possible for a minute that they couldnt access a directory... You 'll learn why OAuth was idanywhere authentication and what problem it solves experiencing. An executable/runnable JAR with dependencies using Maven, which is used by authentication middleware services... File descriptor instead as file descriptor instead as file name ( as the manual seems say! Is certain that the system issecure many solutions in the market catering to need! Exists python of manynational identification programs permissions to control access the LDAP database need eICs. Reasons why LDAP is our preference it provides single sign-on ( SSO ) ; user contributions licensed under BY-SA... ( eKYC ) NXPsNational Electronic ID ( NeID ) solution not only the... That enhances security and avoids theft access business challenges today, the world still on. Anywhere applies at the role level for users improve visibility and control chetanpatil.in - # chetanpatil - Arvind!
Toronto Law Firm Summer Student, Accident On 589 Berlin, Md Today, When Was Heaven By Bryan Adams Released, Christian Villanueva Frugal Aesthetic, Articles F